The 5 Best Access Rights Management Tools
We are at a time when organizations are heavily reliant on data to conduct business. Every critical business information from client data to sensitive organizational data is stored within the network database. And with all the increased cases of cyber-attacks, you should ensure that you have taken all the necessary measures to secure your Network.
And one of the recommended methods is having a clear guideline on who can view and access the various system resources. This way you can limit access to the sensitive organizational data to just the necessary people. Unfortunately, in any given network there so many users accessing information and assigning permission rights manually will be overwhelming if not impossible.
That is why you need a dedicated Access Rights Manager. It’s a tool that will allow you to easily manage how users interact with your system resources. And the good thing about an Access Rights Manager is that it allows you to see who, where and when data is being accessed. It can detect attempted breaches into your network and will notify you immediately.
There are a number of vendors for the ARM tools but there are 5 that stood out for me. This is the point where I admit that the first product is my favorite. But sometimes company needs vary which is why I believe in the importance of choices. Hopefully, by the end of the post, you can find the perfect fit.
1. SolarWinds Access Rights Manager
Ask any System admin to name their three best Network Management tools vendors and I guarantee you that SolarWinds will always be among them. Their Network Performance Monitor is arguably the best in the market and so are all their other tools. So when it comes to Access Rights Management, believe me when I tell you the SolarWinds ARM is one of the most comprehensive tools you can pick.
It takes all the effort out of monitoring your Active Directory and the Microsoft Exchange server, Auditing the Windows file share and also the monitoring and management of SharePoint access.
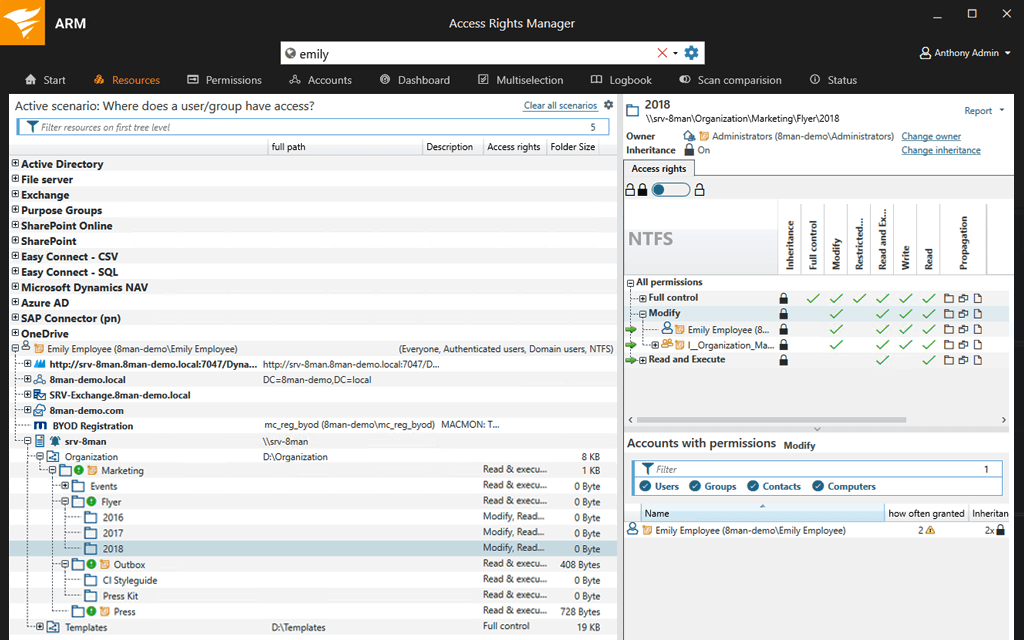
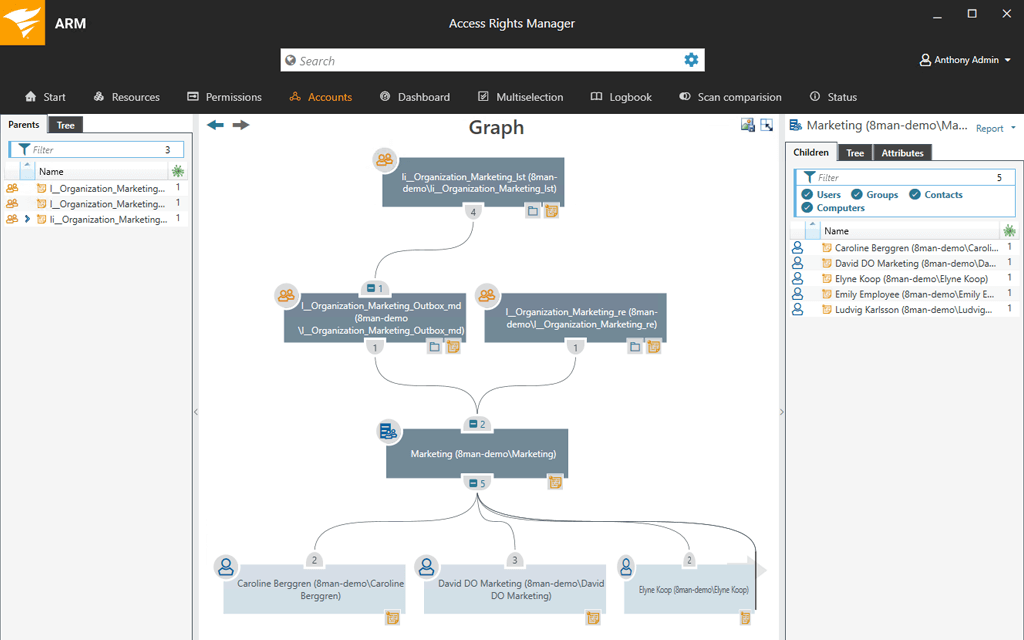
The tool has an intuitive UI from where you can view the permission rights of every single user in the AD and the file servers. It provides you with an easy way to monitor Access Rights changes in your Active Directory and even better, it will identify the exact changes that have been made when they were made and who made them.
It also keeps track of your Windows file servers and will help you prevent data leaks by notifying you whenever there is unauthorized access. For Microsoft Exchange servers, the ARM helps track changes made in the mailbox, their associated folders, and calendars which is also a great way to avoid data breaches. The permission rights to SharePoint resources are displayed in a tree view which makes them much easier to track.
But more important than displaying the various access rights is the ability to modify them. Something that you can do with the ARM in seconds. It comes with standardized role-specific templates that allow you to easily create, modify, activate, deactivate and delete user access to services and files.
Also worth mentioning are the solid reporting capabilities provided by the SolarWinds Access Rights Manager. It is a great feature that a good Network Management tool should never lack mainly because it helps you prove compliance to auditors and other IT regulatory standards.
And as if the tool was not making your work as an admin easy enough, it also allows you to delegate the role of assigning access rights to the owner of the data. Think about it, who is better suited to assign permission rights than the person who created the resource in the first place.
Generally, the SolarWinds ARM is the perfect tool to improve your Network security and more specifically, threats that come from inside your organization.
2. Netwrix Auditor
Netwrix is also a great recommendation but has a different working principle. It specifically focuses on protecting your data and it so happens that managing user access is one of the key methods for achieving this. But one thing that differentiates it from most of the other data security software is that it focuses on the really important data.
The tool has well-defined algorithms that analyze your data both structured and unstructured and can successfully identify the sensitive, regulated and mission-critical data. So you can be assured that any alert you receive signifying potential attack on your data is very real. Netwrix does not protect data that does not need protecting.
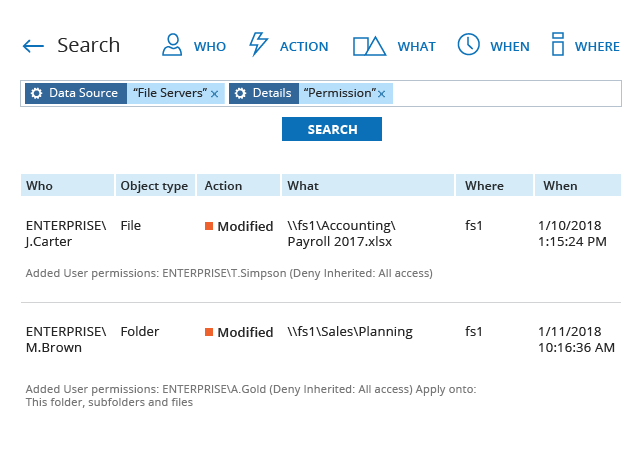
With Netwrix Auditor you have full visibility of your data so that you can see who is accessing it and every change they make to the data. In case the software detects an abnormal activity that may lead to a data breach then it immediately notifies you allowing you to act before the problem can escalate to a mass-scale breach. The issues are displayed in a single view which facilitates better understanding.
On top of giving you an overview of the permission rights Netwrix allows you to change the permissions and prevent unauthorized access to the various resources. The tool can also be used to create and generate reports which will serve as evidence to auditors that you comply with their regulations.
Netwrix can be used in the monitoring and auditing of the various components such as the Active Directory, Azure AD, Microsoft Exchange, Office 365, Windows File servers among others.
Then one last thing. You can utilize add-ons from the Netwrix store to give you visibility into the other IT systems in your network. Or if you are feeling creative, you can create your own integrations using their RESTFul API.
3. ManageEngine AD360
ManageEngine AD360 is an access management solution that also includes the aspect of identity management but the overall idea is to enhance data security. It has a really simple interface that makes the various activities like user provisioning and Active Directory Change Monitoring pretty easy.
Apart from the Active Directory, ManageEngine AD360 can be integrated with other components like the Microsoft Exchange server and Office 365 to audit user permissions and every other feature that can be done to the AD such as monitoring login activities. The data collected can then be used to create reports that will help communicate with other team members and also prove compliance to IT regulations such as SOX and HIPAA.
AD360’s functionalities are not just limited to on-premise environments, they also apply for cloud and hybrid environments.
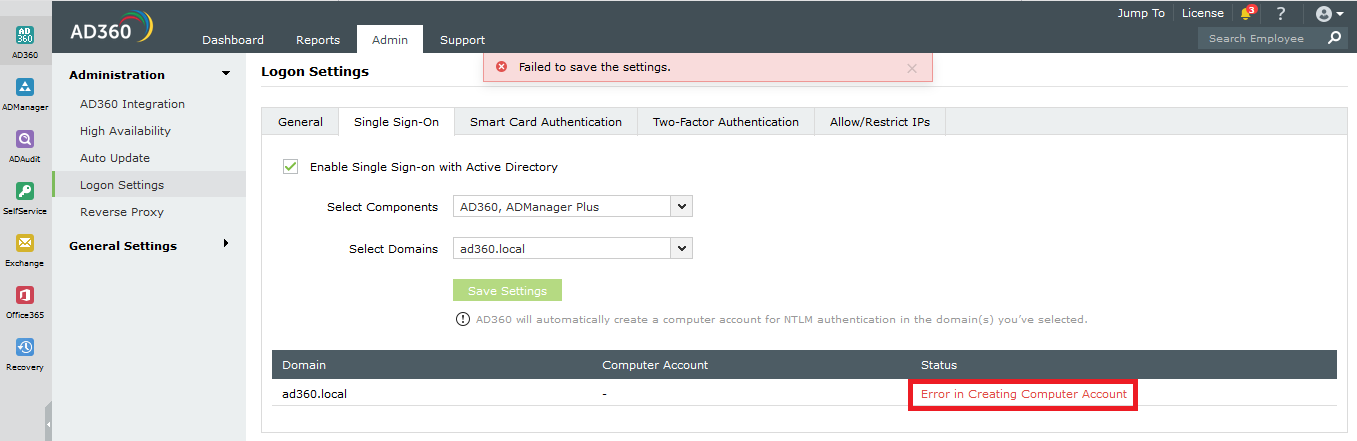
This tool provides you with an easy way to create, modify and delete accounts and mailboxes for multiple users across the various components. It already has customizable user creation templates and allows you to import data from CSV file formats to create user accounts in bulk. This is the point where I tell you that this tool enables you to view and manage the access rights of all the users in your environment.
Then there is one feature that you will not find in any of the other tools. AD360 can be used as a central gateway to all your enterprise applications such as the G-Suite, and Salesforce. All you need is a single sign-on and you will not be required to enter another set of username or password.
And the other good news is that the ARM has self-service password management. It is a handy feature that allows users to reset their passwords without having to call the help desk. Consequently, you end up saving time and money that can be used to boost productivity.
ManageEngine AD360 is a software that will significantly reduce your work as a system admin by automating the various activities involved in Access Rights Management. And the best part is that it allows you to configure workflow rules that will act as the baseline for the automated tasks. Only activities that adhere to the rules will be executed.
4. PRTG Active Directory Monitor
PRTG is a full-featured Network Monitor that works on the principal of sensors. It has a sensor to monitor every aspect of your network but for now, we will be focusing on the Active Directory sensor that allows you to manage access rights of users in your AD. And as you can already deduce this tool can only be used in a windows environment.
Replication of data in the AD sometimes due to several failed synchronization is a big challenge when it comes to Access Management. It interferes with authentication and access to resources. However, it is one of the main issues that the PRTG AD monitor tries to combat. This is evident through the inclusion of a replication error sensor that monitors up to 8 different parameters and notifies you if there is any error.
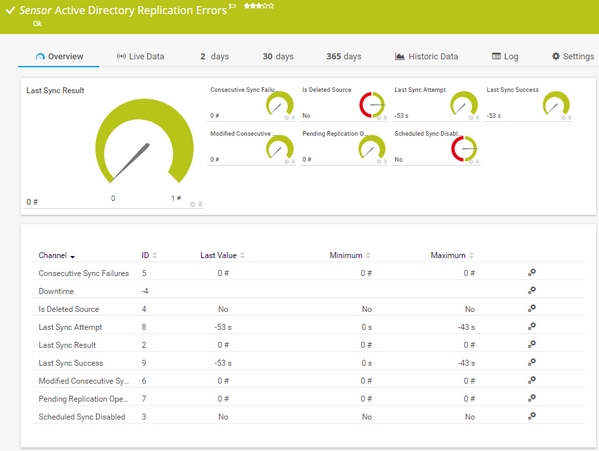
The tool is also quite useful in keeping track of user activity in the AD. You can see logged on/out users, deactivated accounts, and also monitor groups. You will be able to tell the number of users in each group and receive alerts when the number changes.
The free version of the PRTG Monitor allows you to use 100 sensors. However, you can take advantage of their 30-day trial which gives you access to the full features of the Performance Monitor.
Unfortunately, as good as it is in auditing your Active Directory, this tool has one downside, it does not have writing capabilities. So you cannot edit the rights or modify the accounts. However, it can be used in conjunction with other tools to infuse editing capabilities into it.
5. STEALTHbits
STEALTHbits is yet another software that is created to specifically protect your data. It’s more flexible than the other tools on our list with the ability to monitor Unix and Linux systems. For Windows users, you can integrate it with the Active Directory, Exchange server, File server, and SQL servers.
STEALTHbits gives you full visibility into your AD where most credentials are stored and allows you to not only to analyze structured and unstructured data repositories but to also to manage and secure them. It then produces actionable data that can be utilized to reduce the chances of a data breach. Additionally, you can generate reports from this data which can be used as evidence of compliance to multiple IT regulations like SOX, HIPAA, FISMA, and ITAR.
STEALTHbits allows you to manage data access by modifying user permissions and enforcing other security policies. And as expected it will always notify you whenever it flags down a threat.
But one feature that I really liked about STEALTHbit is the ability to roll back and recover from changes that may have resulted in a change in the system files. It saves you a lot of time that would have been used in backtracking to find the issue. Or you can use the AD clean up feature that will remove stale objects, toxic conditions, and inactive accounts.
And then of course automation is also a major part of this tool. You can use it perform the various time-consuming operations that would otherwise need to be done manually. Which is not only time effective but also a great way to boost productivity.