How to Play Any DRM-Protected WMA File [Easy Guide]
In today’s digital world, replicating and distributing digital content presents challenges for content creators and rights holders. To protect intellectual property rights, the Digital Rights Management (DRM) framework was established.
DRM ensures that protected files require proper authorization for access. In this article, we explore the challenges of DRM-protected WMA files and provide solutions for accessing and converting them.
DRM-Protected WMA File: What is it?

For regular PDF files, by-passing is not a big issue. However, when it comes to WMA (Windows Media Audio) files, many users still struggle. A DRM-protected WMA file is an encrypted audio file in the Windows Media Audio format that incorporates DRM technology to enforce access control and usage restrictions.
Most likely, you are also on this page because you were facing the issue of DRM-Protected WMA files. So, let’s begin!
Disclaimer: In the United States, the Digital Millennium Copyright Act (DMCA) is a critical legislation that provides a legal framework for protecting copyrighted works in the digital realm. It criminalizes the circumvention of DRM technologies and prohibits the distribution of tools or services that facilitate such circumvention.
How to Play DRM-Protected WMA Files?
DRM-Protected WMA Files can be decrypted using third-party decoding software. While other methods are also present, such as using Windows Digital Rights Update Tool ⓘ, it is no longer viable because they are not supported beyond Windows 10.
Use a Third-Party Converter
The easiest and most straightforward method to unlock a DRM-protected file is to use software such as tools from Leawo, which convert the audio/video into an unlocked format that can be readily played and accessed.
Step 1: Download Leawo
Leawo is a reputable software provider that offers a tool that is used for DVD ripping and conversion, video conversion, Blu-ray ripping and conversion, and removing DRM protection from audio and video files. Download Leawo Prof. DRM from the official website. This is the specialist tool used for DRM-protected files.

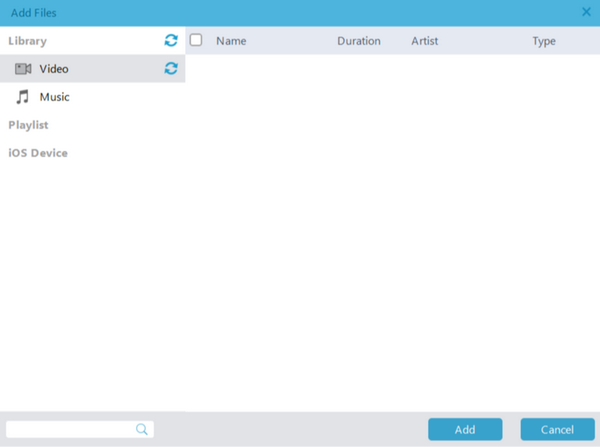
Step 2: Add DRM WMA File to the Program
Launch the program and select the “Add Files” option. Next, choose how you want the output conversion of these files to be. Some of the possible options include M4A, MP3, M4B, AAC, WAV, FLAC, AA, and AAX audio files.
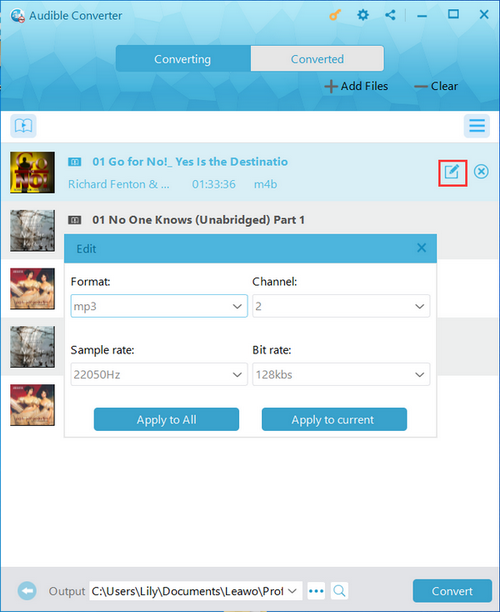
Step 3: Convert
Choose the desired settings for the output. Press “Convert” and you will see your files getting converted instantly without any drop in the quality. They will be stored at the location you chose in the bottom part of the screen.
Alternative Tools
It’s important to know that Leawo is not the only program out there. There are several others which include:
- Aimersoft DRM breaker
- AnyMP4 Video Converter Ultimate
- Microsoft DRM Removal Tool
Why Is This Technique Useful?
Using a DRM-removal software like offers several benefits, including:
One-Time Fee
Accessing DRM-protected WMA files often requires acquiring expensive individual licenses. However, with DRM-removal tools, users can avail themselves of a one-time fee which grants them comprehensive access to the program and the ability to work with various DRM-protected files effortlessly.
By adopting such tools, users can enjoy the benefits of uninterrupted access to a wide range of DRM-protected content without the burden of recurring expenses. This approach provides a cost-effective and convenient solution for managing and utilizing DRM-protected files.
No Loss in Quality
Modern DRM-Removal programs utilize advanced technology to ensure high-quality conversion of DRM-protected WMA files. They retain the original audio quality preserving the nuances and clarity of the music or audio content.
Wide Format Support
One of the main aspects of DRM-removal software is that it allows you to convert WMA files from a wide range of sources. One can easily enjoy offline songs from Spotify without any limitations. Likewise, they also work well with Audiobooks and convert them into accessible audios.
Leawo has the ability to decode iTunes music, liberating iTunes music songs from DRM restrictions. This gets them the freedom to play their iTunes music on any media player or mobile device for unlimited enjoyment.
Batch Conversions
Let’s say you have 20 files that are DRM protected. Getting each one’s license is not only expensive but also quite time consuming. Using a DRM-removal program, you can convert multiple DRM-protected files at once thanks to the batch processing technology incorporated in the program.
Regular Updates
As time passes, the DRM technology framework is improved making it difficult for software to decrypt the music. However, these tools are also updated regularly making them effectively useful for the users.
For instance, if you are unable to convert a music file, a DRM-removal program offers a music recorder technology which records the music being generated by your input audio streams and computer system audio.
This means that even if a file is protected using advanced DRM, it can be simply recorded by the program, which helps in eliminating the protection.

How Does DRM Work on WMA Files?
Many might wonder why they can’t access WMA files without using a third party solution. To answer this question, it is important to learn how DRM works for WMA Files.
Encryption
WMA files are protected under Advanced Encryption Standard (AES). The specific variant of AES used for DRM-protected WMA files is AES-128. The “128” in AES-128 refers to the key size (128 bits). AES-128 is used for protecting WMA files because it is considered highly secure and is widely implemented in the industry due to its robustness and efficiency in protecting sensitive data.
Earlier, Windows Media Digital Rights Management was used as the encryption technique which is why there were security loopholes as well. Older versions of WM-DRM used Windows Media Encryption (WME) which utilized the RC4 stream cipher ⓘ for encryption.

Enforcement of Usage Rules
DRM also imposes usage restrictions specified in the license. These restrictions include limitations on the number of devices the file can be played on, restrictions on copying or sharing, or the ability to expire the content after a certain period.
For example, if a user attempts to play a DRM-protected WMA file on a fourth unlicensed device, the DRM system would detect the unauthorized access and deny playback. Similarly, if a user tries to make unauthorized copies or share the content, the DRM system would intervene and prevent those actions.
In some cases, time enforcement is also put to practice. A license is provided to the users which allows them to access the content for a specific duration such as 30 days from the first playback.
Authentication

WMA files are also protected with authentication protocols enforced via DRM. Authentication involves verifying the user’s credentials and checking the validity of the license associated with the file. This process ensures that only authorized users or devices can decrypt and play the protected content.
In certain cases, the DRM system communicates with a license server to perform the authentication process. This process involves sending the user’s credentials to a specific license server. This server responds with the status and permissions associated with the license.
This process adds an extra layer of security and ultimately prevents unauthorized users or devices from decrypting and accessing the protected content.
Conclusion
DRM plays a critical role in protecting WMA files and enforcing usage restrictions. DRM employs encryption, authentication, and enforcement of usage rights mechanisms to ensure the data is protected. It also utilizes licensing to specify the rights and permissions associated with the content. Tools such as Leawo offer effective solutions for accessing and managing DRM-protected WMA files, as explored in this guide.
DRM-Protected WMA Files - FAQs
Digital Rights Management is a technology that protects digital content like Windows Media Audio (WMA) files by encrypting them and enforcing usage restrictions. It ensures that only authorized users can access and listen to the audio.
Authentication is the process of verifying the user’s identity and validating the associated license. Generally, it is performed using password access. Users provide their credentials and these are checked against the license to determine authorization. Upon successful authentication, the DRM system retrieves the decryption key required to unlock and play the protected content.
DRM-protected WMA files have limitations which include device compatibility restrictions, complexities in license acquisition and management, and other potential vulnerabilities as well.
 Reviewed by
Reviewed by 




