How to Automate Network Audits for Network Compliance using Solarwinds NCM?
To find the inefficiencies and security issues on the Network, conducting auditing is essential. Before taking part in the compliance team’s audit review, Network Administrators can use the Compliance Policy Reports feature available in Solarwinds NCM to conduct internal audits to showcase network control and operation management’s success to the compliance team.
Compliance Policy Reports give network administrators the advantage of ensuring all devices comply with the internal policies and standards. We can enforce one or more rules in a policy report to scan for violations. Also, we can include the remediation steps to ensure the devices comply. To learn more about Solarwinds NCM and its features, click this link.
How to Configure Compliance Policy Reports
To configure policy reports, we need policies, and to create policies, we need rules. Each policy report has one more policy, and each policy has one or more rules. The below image can make us understand better.
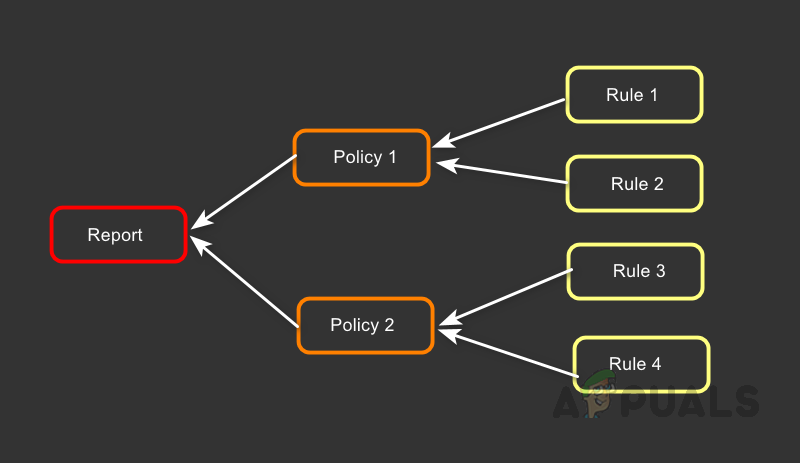
We can use a rule in multiple policies and a policy in multiple reports. So to configure a Policy Report, we need policies and rules. Now let’s see how to create rules and policies.
Creating a Rule
A rule contains the conditions a device must or must not have. Also, we can include remediation commands if the rule is violated. To create a rule, follow the below steps.
- Go to Settings and click on All Settings.
- Click on NCM Settings under Product Specific Settings.
- Click on Manage Rules under Compliance Policy Report Management.
- We can see a lot of pre-configured rules under Manage Rules.
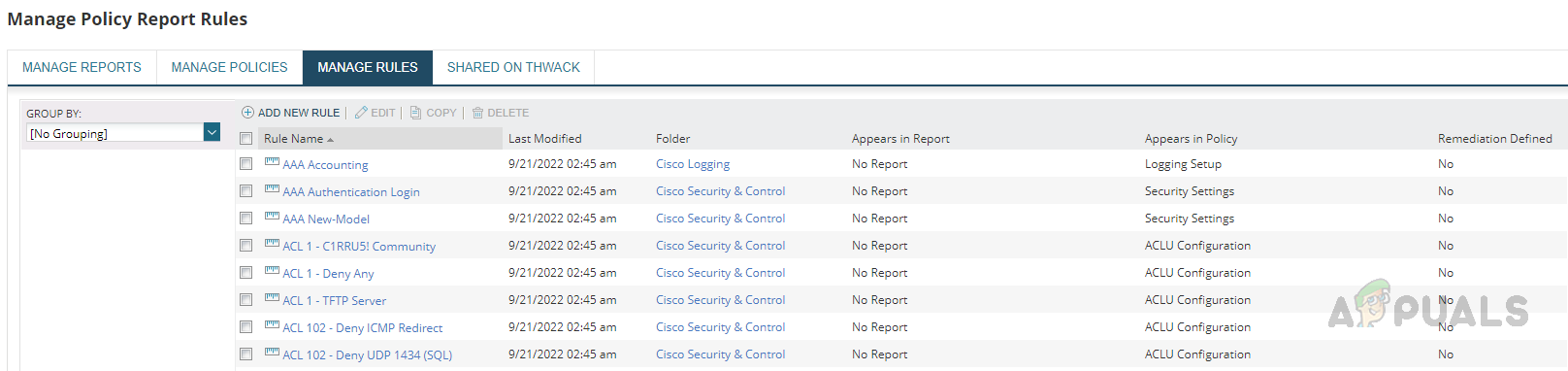 We can also use these pre-configured rules to run our policy reports based on the needs. Also, we can customize them depending on our internal policies and standards.
We can also use these pre-configured rules to run our policy reports based on the needs. Also, we can customize them depending on our internal policies and standards. - To create a new rule, click on Add New Rule.
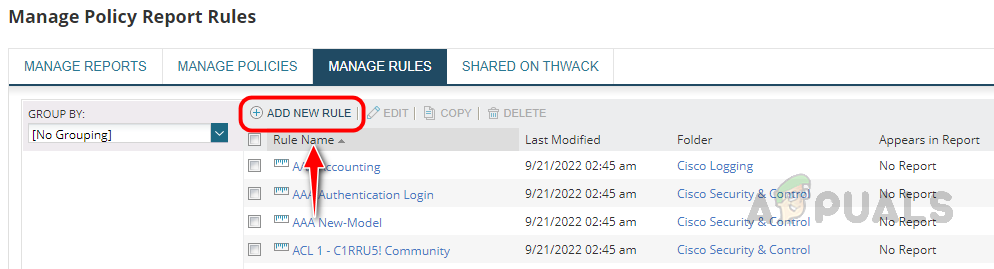
- On the create new rule page, provide an appropriate name and description, choose the alert severity level, create a new folder to store the rule, or use an existing available folder. You can place rules in the same folder which are part of the same category.
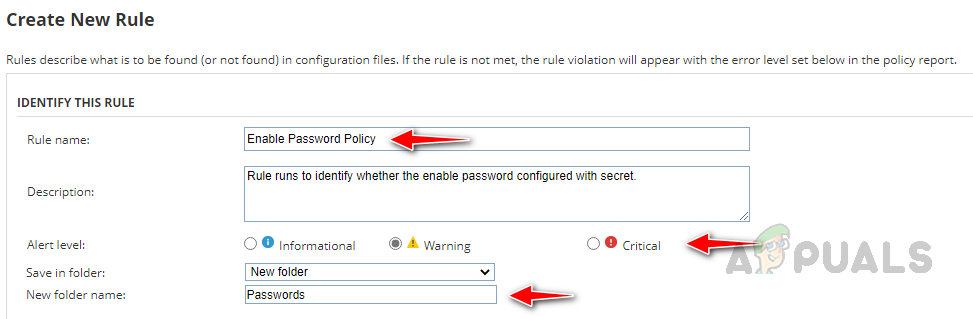
- In the String Matching section, select the applicable from String is found or String is Not found. In this demo, let’s validate enable password configured with the secret option. Hence I have chosen String is NOT found.
In the String section, enter the string that we want to match in the string section.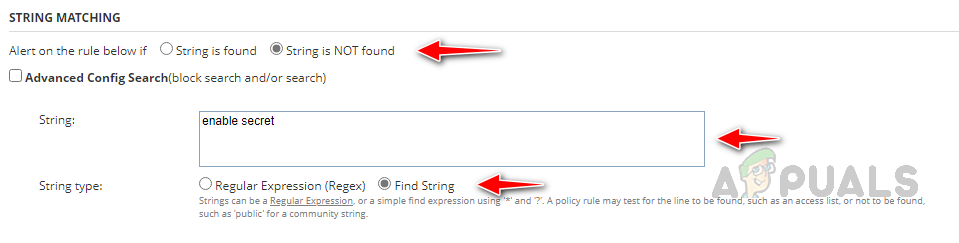
In String type, choose Find String since we are using strings. We can use the Advanced Config Search option to create advanced rules with and/or operators. Find examples in this link on how to use the advanced option. - In the Remediation section, enter your remediation commands. Select Execute Script in Config Mode to run the config mode commands.
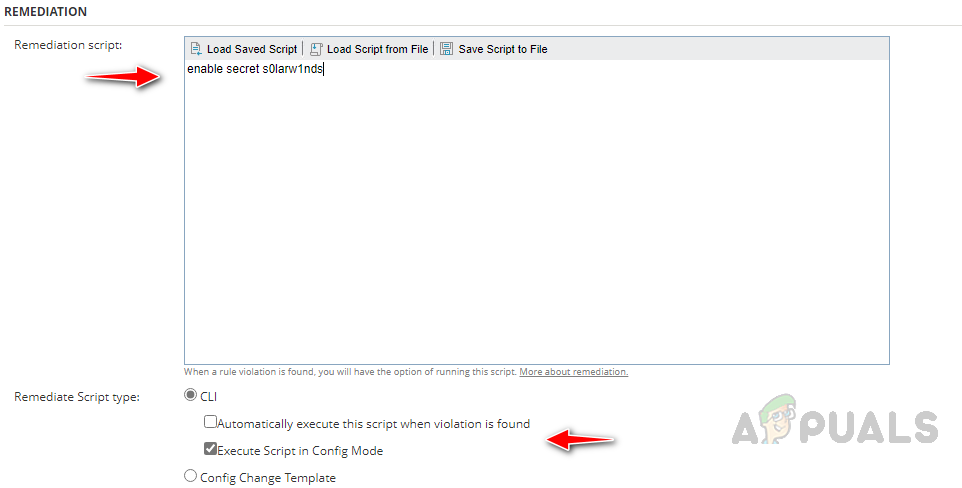
Select Automatically execute this script when a violation is found to automate the remediation step. If you want to review the report and then you want to apply remediation if necessary, uncheck this option. - Click on Test to validate whether our rule is running fine.
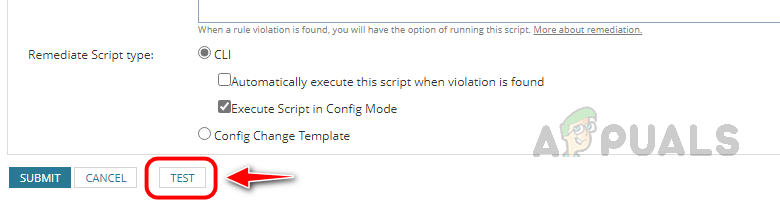
- Select a config file from a node for the Test and click on Test Rule Against Selected Config.
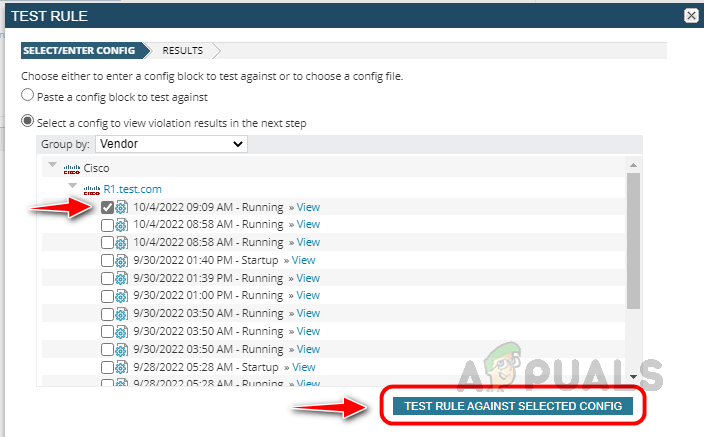
- Validate the result to make sure the rule is working fine.
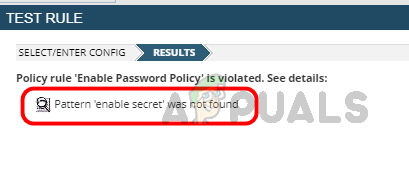
Here, our rule is working fine, as expected. - Click on Submit to save the configured rule.
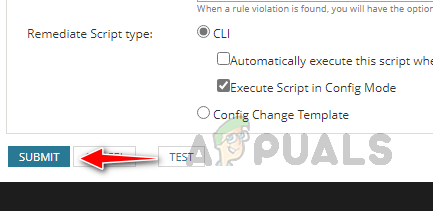
We have configured the rule. Now let’s see how to add this rule into a policy.
Creating a Policy
A policy has more than one rule and devices and config types to which the rule needs to be audited. Follow the below steps to configure a policy.
- In NCM Settings, click on Manage Policy under Compliance Policy Report Management.

- Click on Add New Policy to create a new policy.
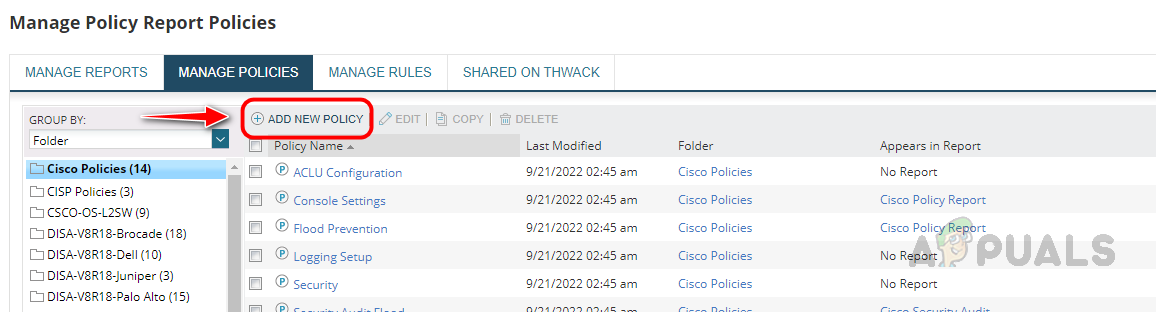
- Provide an appropriate name for the policy. Choose an existing folder to save the policy or create a new one. We have three options for choosing the devices, use All nodes to run this policy against all the nodes in monitoring, use Select nodes to determine any specific nodes, and use Dynamic selection to choose the nodes based on some criteria we want.
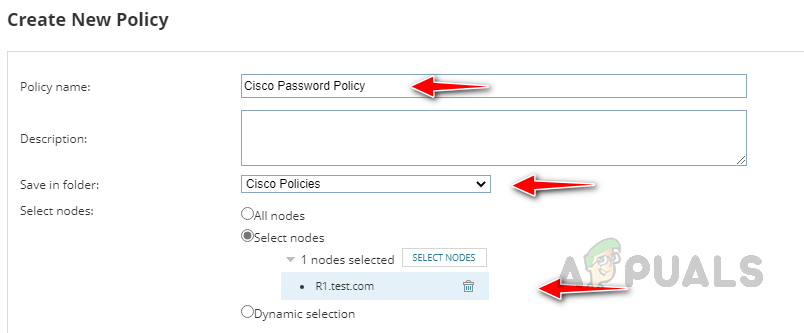
- In Search most recent config type, choose the preferred config or use any recently downloaded config. In the All Policy Rules section, select the rules you want to add to this policy and click on Add. We can add multiple rules to a policy. Click on Submit to save the configured policy.
Now our policy is configured, let’s see how to create the policy report.
Creating a Policy Report
A policy report is the collection of related policies, it runs against the config type for the specified node in the policy to identify any violation in the configured rule. We can add multiple policies to a policy report. Follow the below steps to configure the policy report.
- In NCM Settings, click on Manage Policy Reports under Compliance Policy Report Management.

- Click on Add New Report.
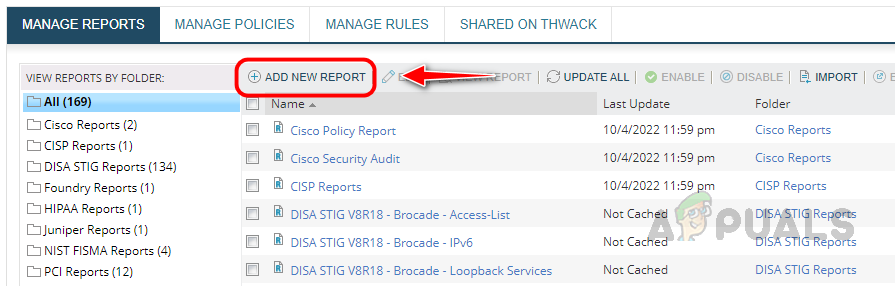
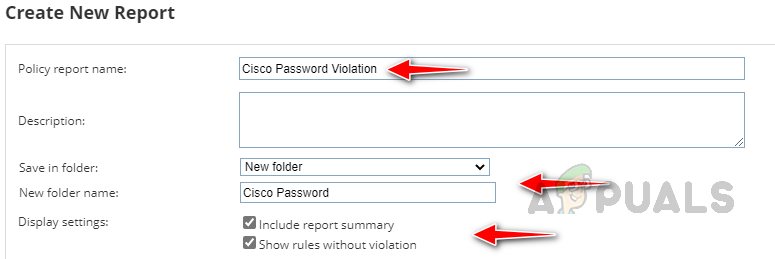
- Provide an appropriate name for the report, use the existing folder, or create a new folder to save the report.
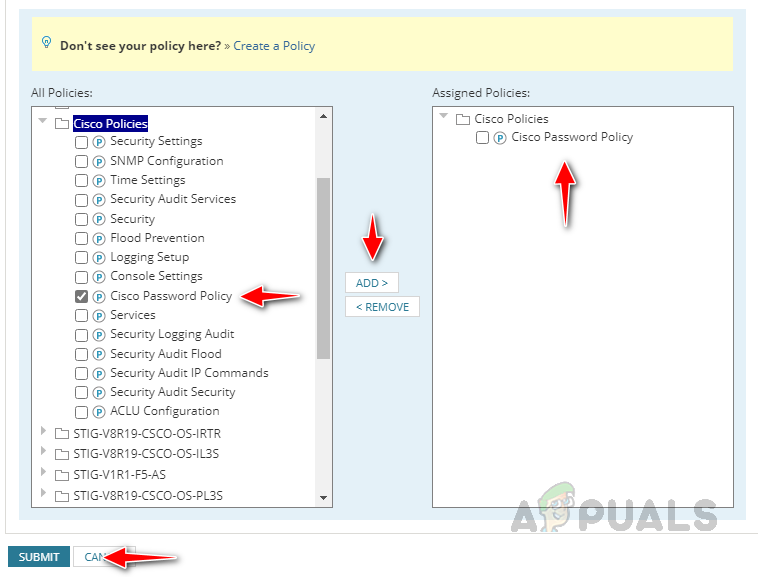
- Expand the folder where we saved our policy, select the policies for the report, and then click on Add and Submit to save the report.
Our policy report is ready. To run the report, we must ensure the policy cache is up to date. To check that, follow the below steps.
- In NCM Settings, click on Advanced Settings under Advanced.
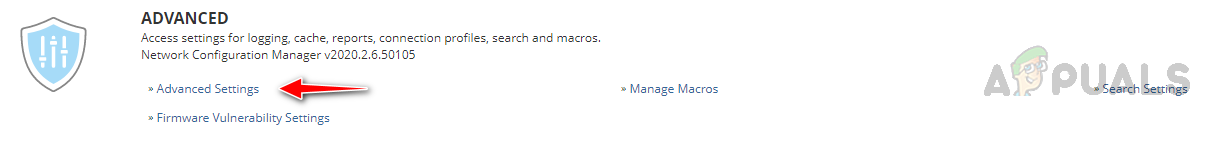
- In Advanced Settings, select the Enable Config and Policy Caches and specify the time when the policy cache to be generated under Cache Settings.
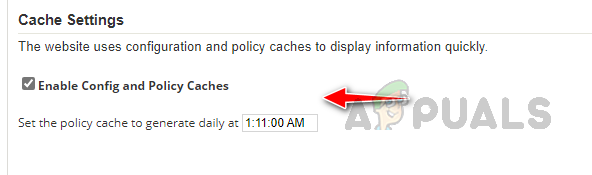
- Click on Submit to save the changes.
- We need to update the cache manually if you still get the below error while checking the policy report.
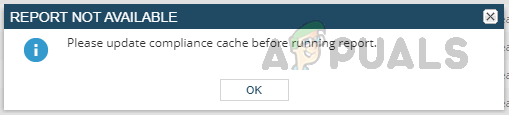
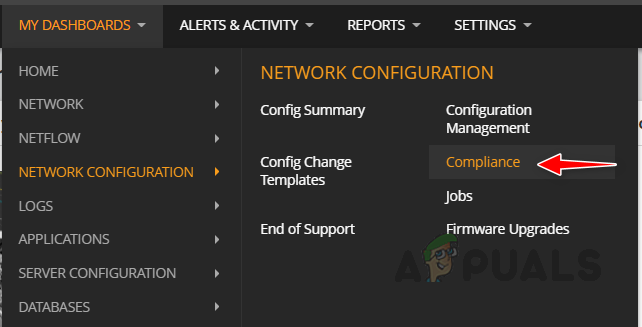
- To manually update the cache, go to Compliance from the Network Config Summary sub-menu.
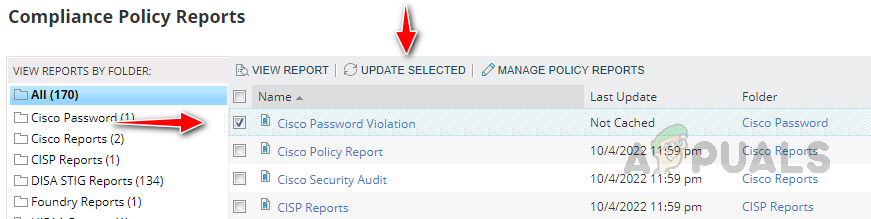
- You can select all reports to update the cache or any specific report and update the cache.
- Once the update is completed, click on the report to open the report.
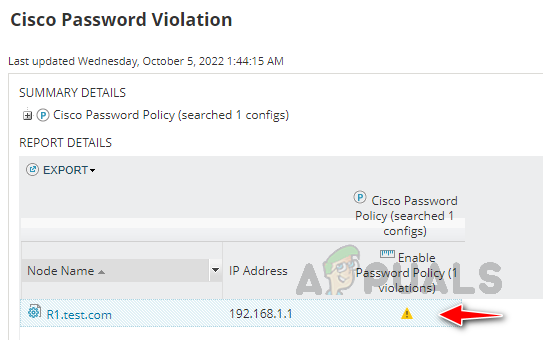 We can see a warning severity for the device. Click on the warning severity to open violation details.
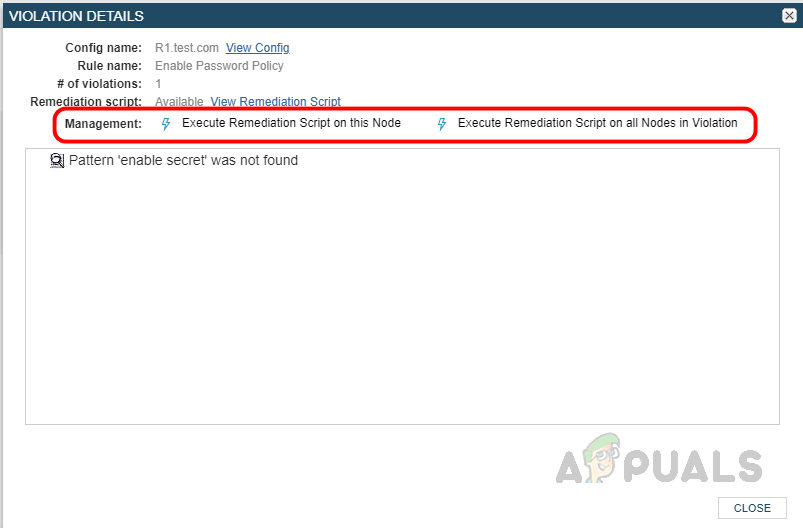
We can see a warning severity for the device. Click on the warning severity to open violation details. - In the violation details, we can see the details, and in Management, we have the option to execute our remediation script for the specific node, or for all nodes, we can choose either of these options to run the remediation script.
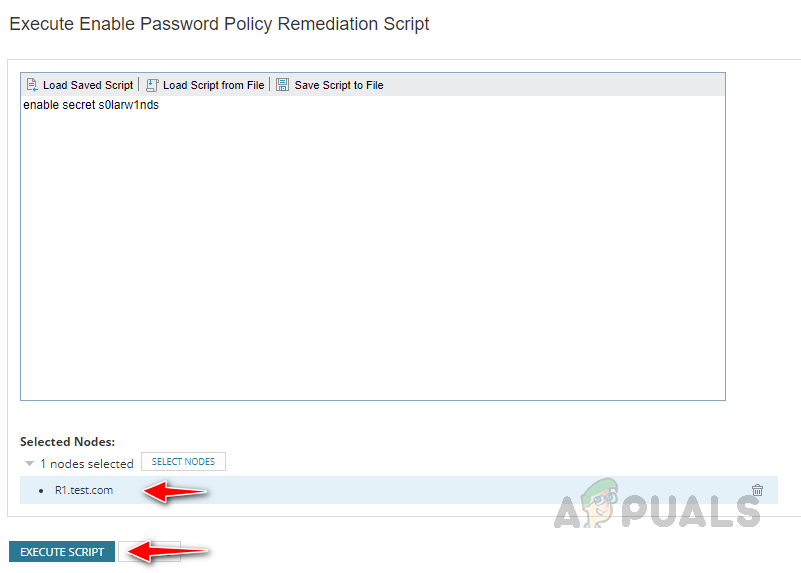
- Once you click on Execute Remediation Script on this Node, a new window will open there, you can see the remediation script and the node we will run the script. Click on Execute Script to run the remediation script.
- Once click on the Execute Script, it will take us to the Transfer Status page, where we can see the result for the remediation script execution.
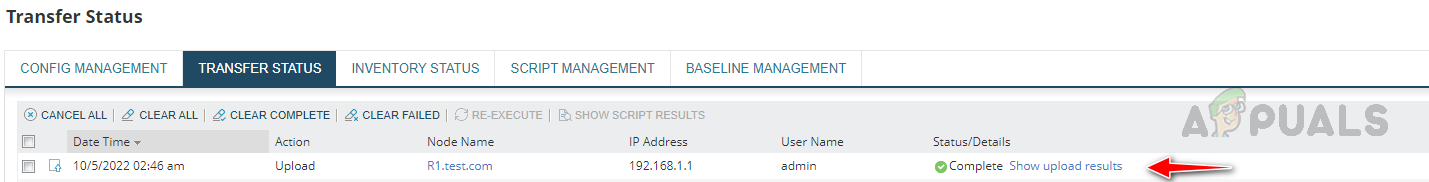
If the execution fails, check the error and fix it to run the remediation script.
To automate the remediation script execution, we need to check the Automatically execute the script when violation is found while configuring the rule.
This is how we can create policy reports to perform the internal audit to comply with the policies and standards of the organization. We can schedule the policy reports to run at regular intervals. To Automate the report, follow the below steps.
Automating Policy Reports
- Go to Jobs from the Network Configuration sub-menu.
- Click on Create New Job.
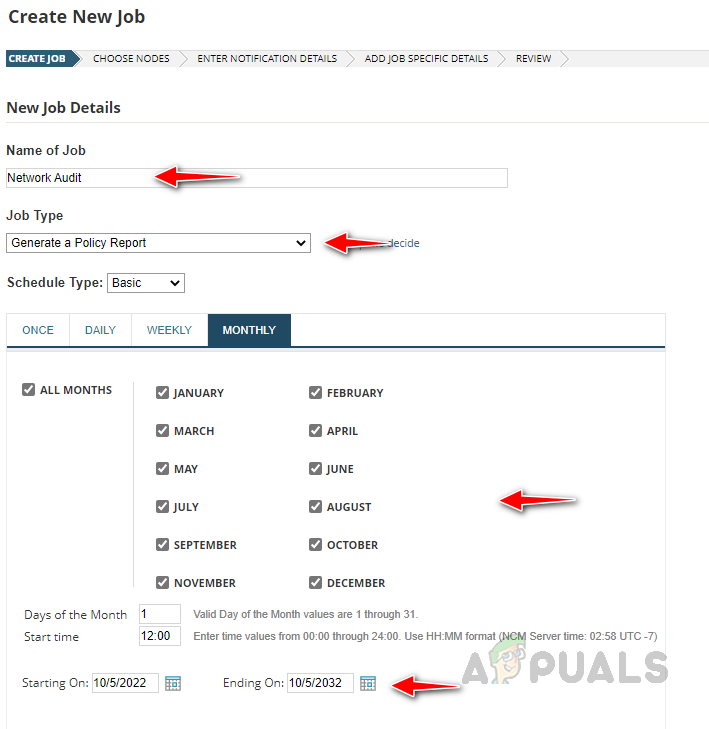
- Provide an appropriate name for the job, and select Generate a Policy Report from the Job Type drop-down. Select the schedule when you want to run the job and click on Next.
- For this job, we can’t select nodes. Since the nodes are already configured in the policy report, click on Next.
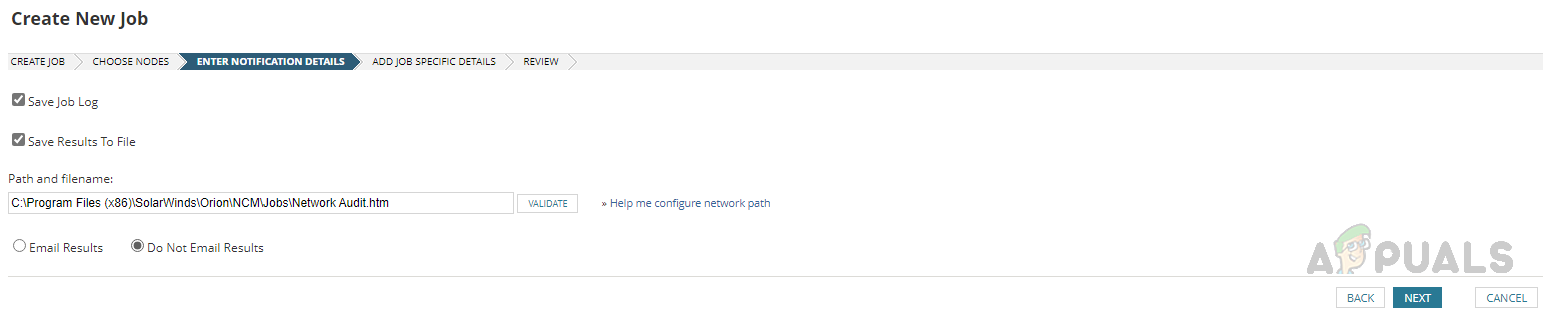
- Select the preferred notification method on the next page and click on Next.
- Select the policy report you want to add to this job and check to Send notification only when there are policy violations to receive a notification only when the rule found any violation in the devices. Click Next.
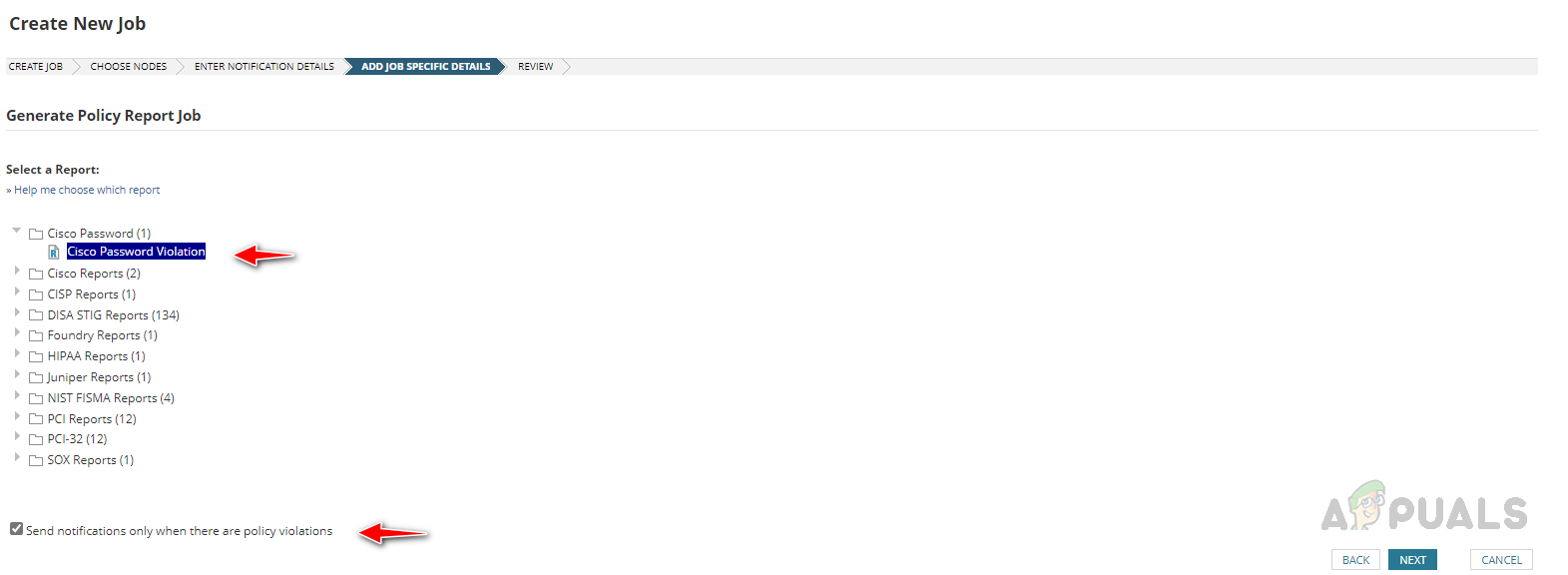
- Review the job details and click on Finish to save the job.
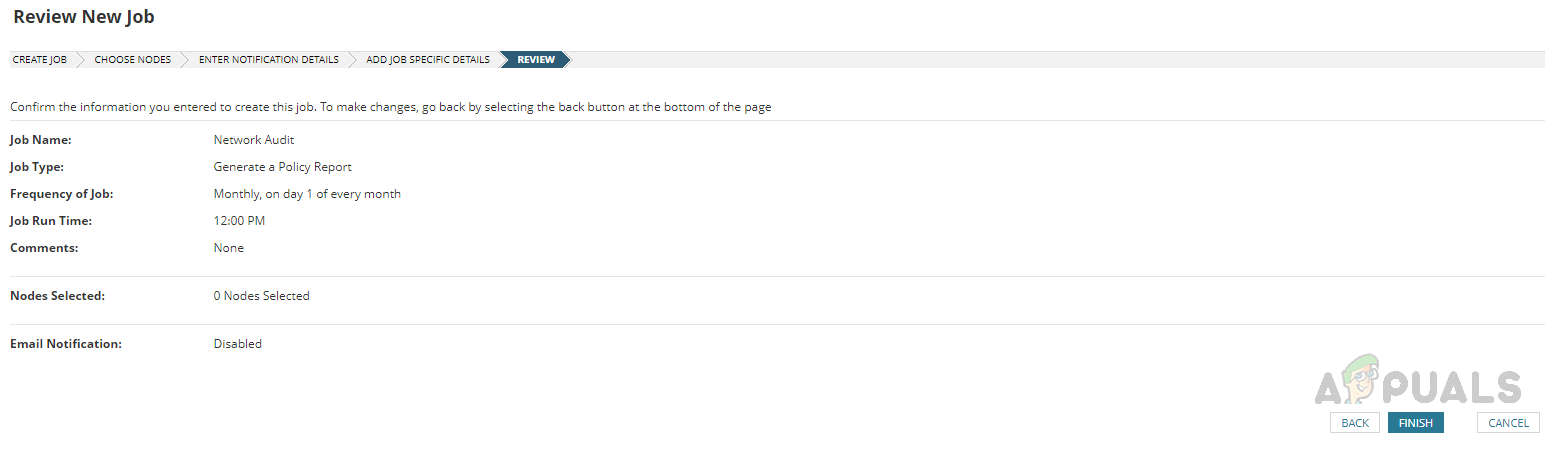
The configured job will run based on the schedule we have chosen. We will receive notification emails whenever a violation is found if we configure the email option in the notification section. We can also review the job logs to check the job details. This is how we can automate our policy reports to keep our network devices compliant with the organization’s policy standards to showcase the success of the network control and operation management to the compliance team.