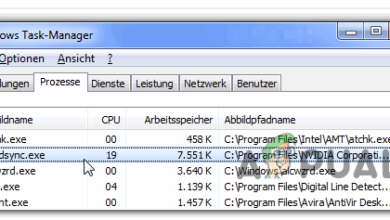
What is remsh.exe and should I delete it?
Some users are debating whether remsh.exe is a malicious executable or a legitimate Windows component. Most of the time, users end up investigating the process after noticing that it’s constantly using the system’s resources – writing and reading stuff on the Windows partition or trying to access the Internet.
But perhaps even more bothersome, a lot of users report that the remsh.exe process is responsible from waking certain systems from hibernation or from sleep.
What is remsh.exe?
The legitimate remsh.exe is a reliability improvement file introduced by the Windows update KB4023057. Remsh.exe was released to address update component issues specifically for Windows 10 Versions 1057, 1511 and 1607. Because of this, you shouldn’t encounter it on all machines that have Windows 10 installed, only those 3 build versions.
Even if this file has a lot of red flags that malware files have (high CPU usage, Big HDD writes, Internet usage), the process is a legitimate Windows 10 file as long as it’s signed by Microsoft.
Potential Security Risk
Even the official Microsoft documentation mentions that the remsh.exe file is susceptible to be used in a phishers scheme if it’s not installed by the KB4023057 update. Because of this, it’s important to make the required verifications in order to determine if the remsh.exe file is legitimate or not.
The quickest way to determine if the file is legitimate is to check if it’s signed in by Microsoft. To do this, press Ctrl + Shift + Esc to open up Task Manager. Then, in the Processes tab, look for the remsh.exe process, right-click on it and choose Properties.
In the remsh.exe Properties screen, go to the Digital Signatures tab and see if the Name of signer corresponds with Microsoft Windows. If it does, you can consider the file safe.
In the event that the remsh.exe file isn’t signed by Microsoft, further investigation is required. To make sure that the file is not part of any phishing scheme, we recommend analyzing your system file with a powerful scanner like Safety Scanner or Malwarebytes to remove any security threat. If you use Malwarebytes, you can use this guide (here) to ensure that you perform a full scan – but keep in mind that it will take a while.
Note: If you’re looking for a quick checkup tool, you can also upload the remsh.exe file to Virus Total for analysis. But keep in mind that this won’t eliminate the security threat – it will only confirm or infirm your suspicions if you believe that you’re dealing with a malicious file.
How to disable remsh.exe?
To be clear, you should avoid disabling the remsh.exe file unless you find that the executable is causing issues with your machine. If you previously connected that remsh.exe is legitimate, keeping it active will contribute to your Windows 10 updates being installed seamlessly and reliably.
However, if you find that remsh.exe is causing High CPU (or hard disk) usage or it’s constantly waking your computer from hibernation or sleep, there are some things you can do to stop this behavior. Just keep in mind that this is not something that Microsoft would advise.
Below you have two different methods that you can use to disable remsh.exe from your Windows 10 computer.
Method 1: Disabling remsh.exe using Autoruns
Autoruns is a neat piece of freeware that enables users to remove startup keys, run keys, runonce keys and registry keys. It’s especially useful in this case since we can use it to prevent remsh.exe from being called and started at every system startup.
Here’s a quick guide on using Autoruns to disable remsh.exe:
- Visit this official download link (here) and click on Download Autoruns and Autorunsc to download an archive of the utility.
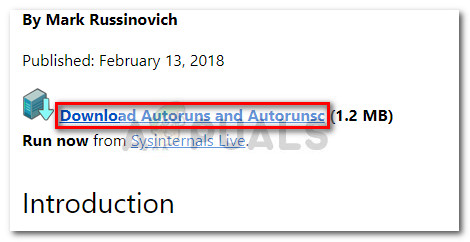
- Once the archive is downloaded on your computer, use a decompression software like WinZip, WinRar or 7-zip to extract the contents of the archive in an accessible folder.
- Navigate to the folder containing the Autoruns files and double-click on Autoruns.exe.
- Wait until the Everything list of Autoruns is fully populated. Once the list is full, press Ctrl + F to bring up the search function.
- In the search box, type remsh.exe and click on Find Next.
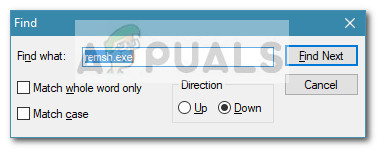
- Right-click on the highlighted entry and click on Delete to remove the startup key associated with remsh.exe.
- Repeat steps 5 and step 6 until you have no mention of the remsh.exe left.
- Close Autoruns and restart your computer.
At the next startup, open Task Manager (Ctrl + Shift + Esc) and see if you still find the remsh.exe process running. If it’s still active, continue with Method 2 to remove it along with the update that installed it in the first place.
Method 2: Uninstalling the Windows Update KB4023057
Another way to go around removing remsh.exe is to uninstall the Windows Update (KB4023057) that installed remsh.exe. Users in a similar situation have reported that uninstalling the KB4023057 update has also removed the remsh.exe and consequently stopped the process from randomly waking their system from sleep or hibernation.
Here’s a quick guide on uninstalling the KB4023057 Windows update:
- Open a new Run box by pressing Wndows key + R. Then, type “ms-settings:windowsupdate” and hit Enter to open the Windows Update screen.
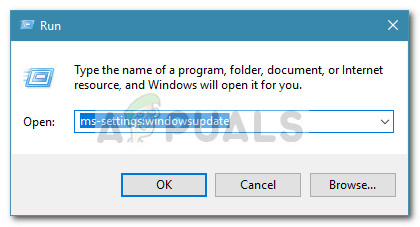
- In the Windows Update screen, click on View update history.
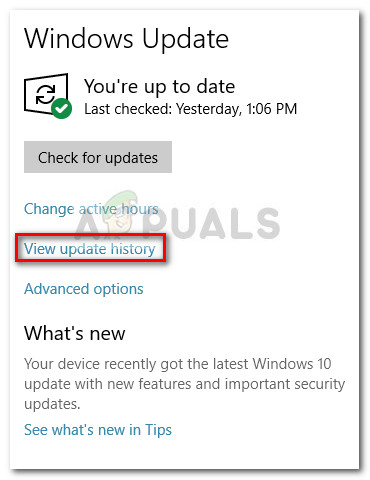
- In the View update history screen, click on Uninstall updates.
- Scroll through the list of installed Windows updates to locate the KB4023057 update.
- Right-click on the KB4023057 and choose Uninstall, then follow the on-screen prompts to remove it from your system.
- Restart you computer. You should noticed that the remsh.exe process is no longer present in Task Manager.