How to Stop User Accounts from Opening Certain Applications, Files and Folders in Windows?
There are times when you need to prevent certain users from opening applications, files, or folders. AppLocker is a security feature in Windows that helps you do this. AppLocker is a part of Windows Professional and Enterprise editions.

In this article, I will show you how to enable AppLocker and use it in your organization.
In order to use AppLocker and create deny rules, we will utilize the Local Group Policy Editor for local computers or the Group Policy Editor for domain-joined machines.
- Hold the Windows logo key and press R.
- Type ‘gpedit.msc‘ and press ‘Enter‘ to open the Local Group Policy Editor.
- Expand Computer Configuration > Windows Settings > Security Settings > Application Control Policies.
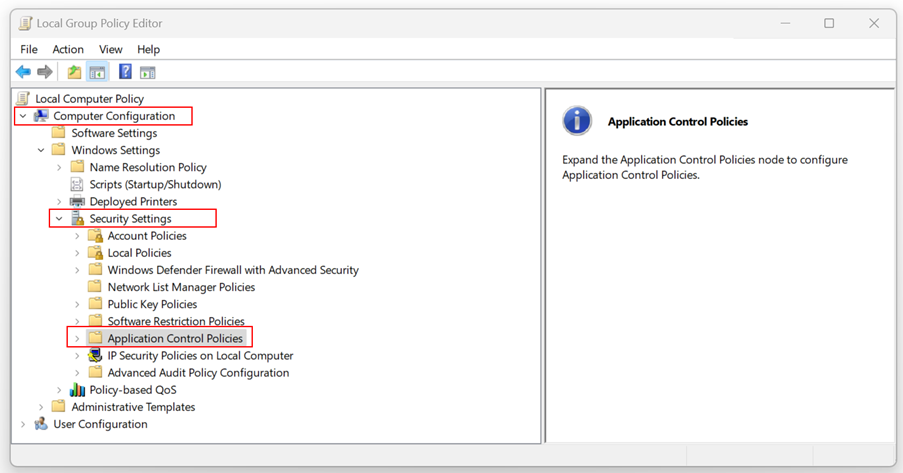
- Expand Application Control Policies > AppLocker.
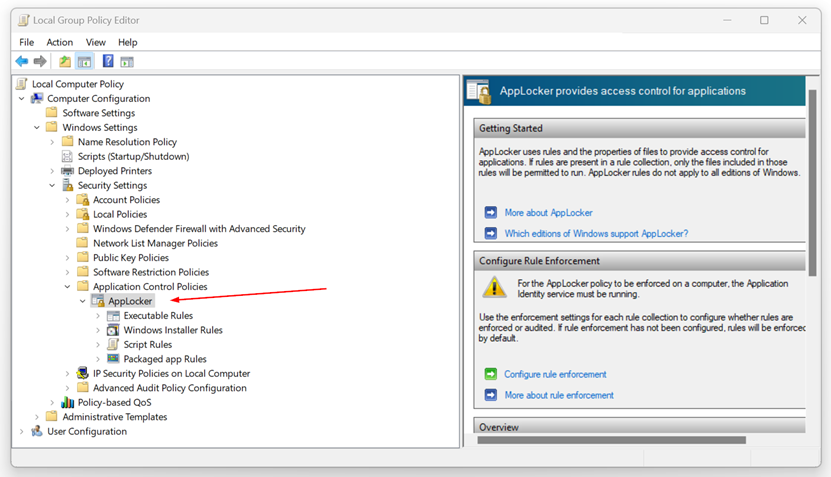
- Right-click on “Executable Rules” and select “Create New Rule…“.
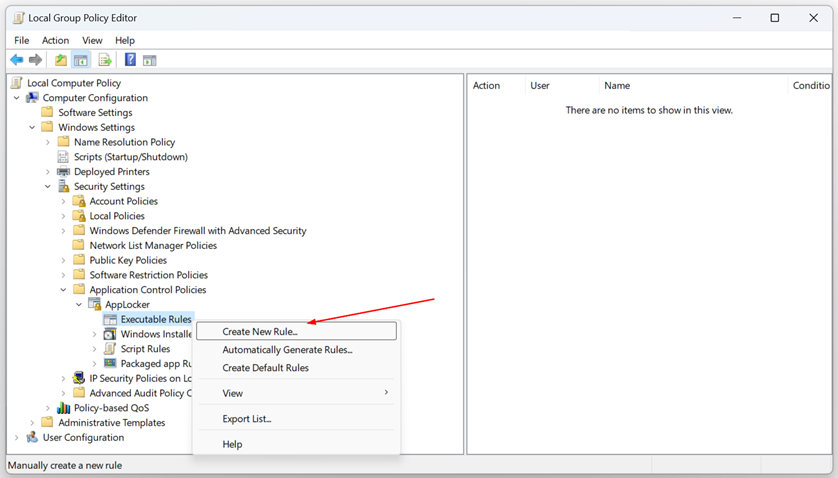
- Under Before Your Begin click Next.
- Under Permissions, click Deny, and then click on Select to choose the account that will be denied access to certain apps.
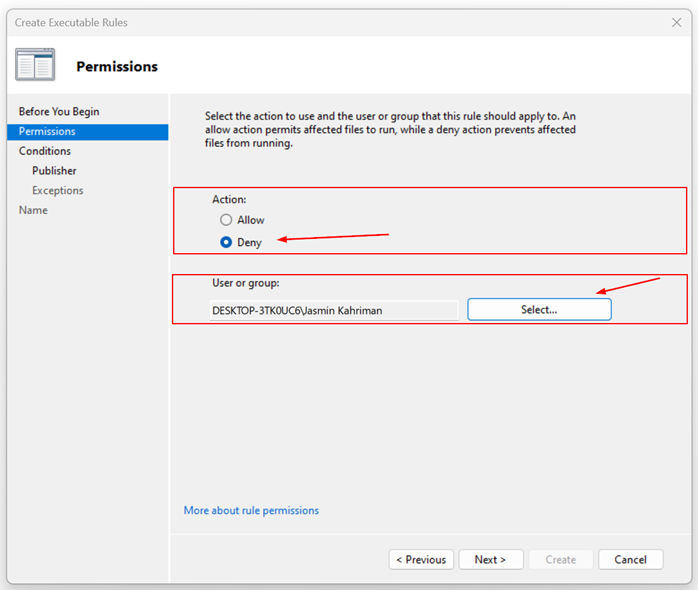
- Select the type of primary condition that you would like to create, and then click ‘Next’. You can choose one of the three conditions: Publisher, Path, or File hash. So, what is the difference?
- Publisher – related to applications signed by the publisher.
- Path – related to a file or folder path.
- File hash – related to applications that are not signed by the publisher.
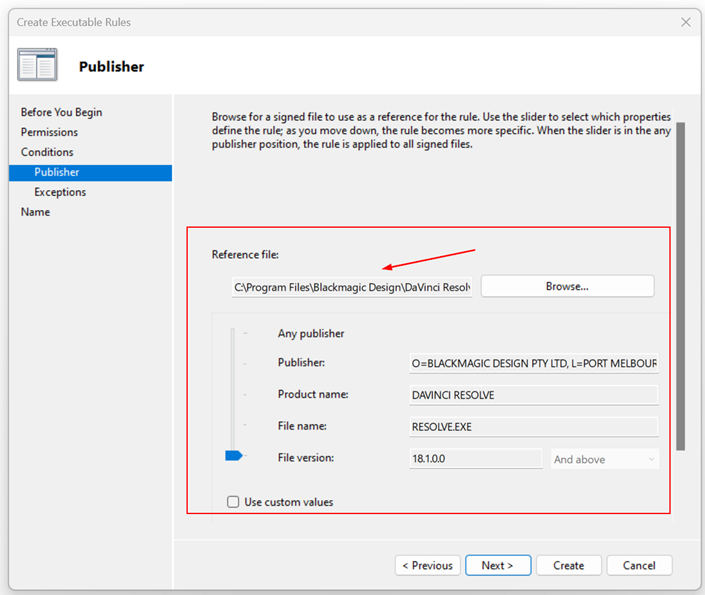
- Under the “Publisher,” click “Browse” to select the reference file you want to deny access to.
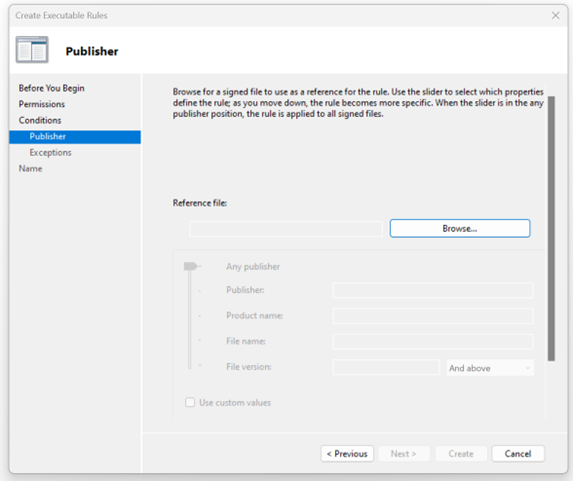
- In my example, I selected DaVinci Resolve software, which is used for video editing. You can also use the slider to select the properties that define the rule. As you move down, the rule becomes more specific. When the slider is in any publisher position, the rule is applied to all signed files.
I keep the default settings for the slider. Once done, click Next.

- You can also add exceptions. Exceptions are optional and allow you to exclude files that would normally be included in the rule. To continue configuring this rule without adding an exception, click ‘Next‘.
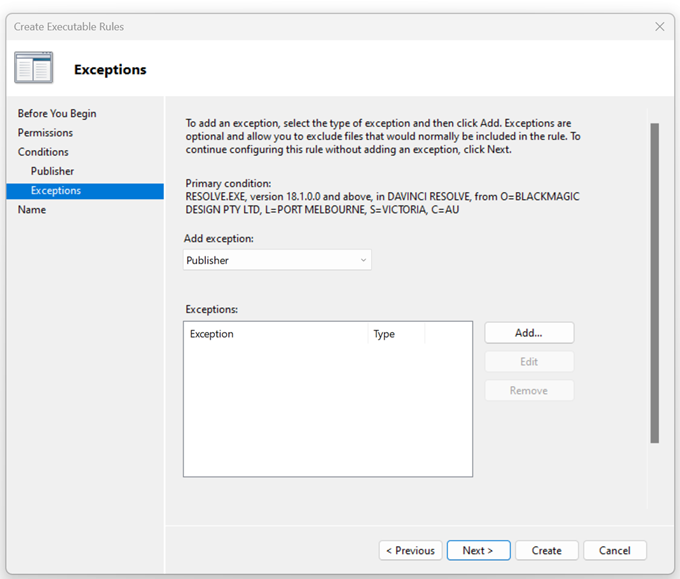
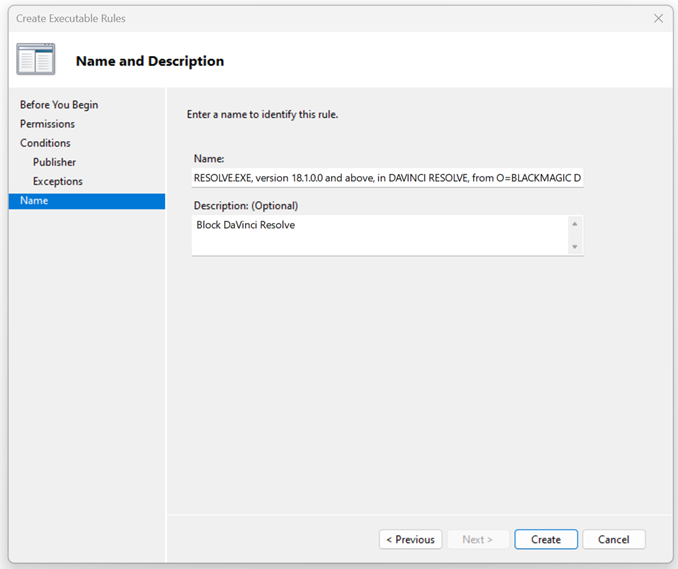
- Enter a name to identify this rule and click Create.
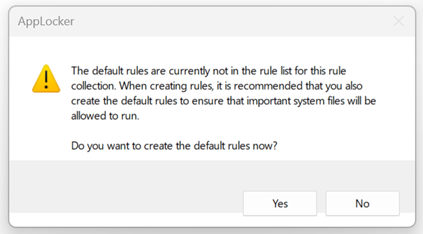
- Under ‘Do you want to create the default rules now?’, click ‘Yes‘. The default rules are not currently in the rule list for this rule collection. When creating rules, it is recommended to also create the default rules to ensure that important system files will be allowed to run.
- You have successfully denied the application of your choice. As you can see, it is listed under Executable Rules.
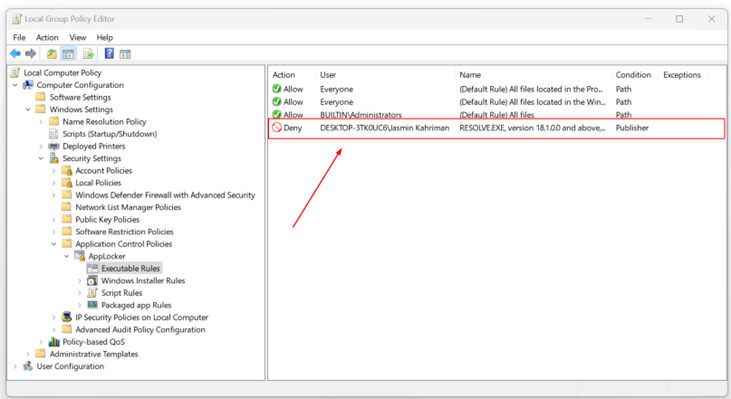
- Close the Local Group Policy Editor.
- Now, when you try to open the app, it will be blocked.
Wrap Up
There are moments when you need to deny certain local or domain users from opening specific applications, files, or folders. By using AppLocker, which is integrated into Windows 11, you can create policies and disable targets by the publisher, path, and file hash.
This article covers step-by-step instructions on how to do it.