What is the Difference Between a Proxy and VPN?
Many users have a different kind of restrictions for connecting to their favorite websites and will be in need of using whether proxy or VPN to connect to it. Both of them work pretty well, depending on the tools that users will be using. However, some users are wondering about the difference between these two. As both of these digital tools are quite similar to each other, there are also differences between them. In this article, we will talk about what a proxy and VPN is and what is the difference between them.

What is a Proxy?
A proxy server is a dedicated computer that receives our request and forwards it to the target website, then sends the received information from the target website back to us. It serves as an intermediary between the user and the target website. The proxy will hide the user’s IP address and use their own to send the request to the target website. By doing so, the user will be anonymous while surfing through the proxy.
Proxies are mostly used when the user wants to be anonymous or trying to reach content that is restricted to their IP address. This provides more privacy for a user that is connected to the internet. However, the proxy will decrypt the traffic and it will not be safe for the client. There are also several types of proxies that are used for different needs as shown below:
- HTTP: The most common proxies that are used to route website traffic only.
- SOCKS: This can also work for traffic like games and applications.
- DNS: This proxy usually works within the device’s internet settings.
- SSL: Similar to the HTTP, but with an added layer of encryption.

What is a VPN?
VPN is similar to a proxy and it creates the connection between the client and the target website/server that is restricted to the client. This will not only work in the web browser but for all the applications. All the traffic that is going from the user to the VPN, and then VPN to the website will be encrypted. This will make sure that all the data will be safe between the client and the website.
VPN also helps to hide the user’s activity from their ISP. Some good VPNs will provide a no-log policy, which ensures that they can’t record, track, or share the user data with a third party. However, some VPNs host servers can still keep the logs of your activity through their VPN. Most of the best and famous VPNs will cost a lot to use. They charge the clients for their VPN usage with monthly or yearly packages.

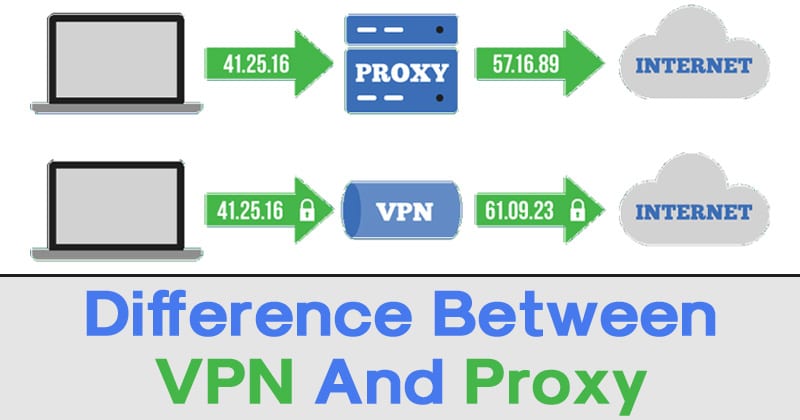
Difference Between the Proxy and VPN
VPN and proxy are both digital tools that let users connect to any website as if they are in different countries. VPN reroutes all the web activity, whereas proxies do not. The proxy will only work on the device that is configured for the proxy and VPN will have application for all devices that work on all the devices/applications to make them secure. Most of the proxies do not support the basic encryption that means the client’s privacy will be less protected and the information can be leaked. VPNs provide encryption and they are specifically designed to protect the privacy of the client.
If the user wants to get access to a website that is only for a little while and does not require sharing any information with the website, then the proxy would be the best choice. It is best to use a proxy for smaller tasks where the user is also not concerned about the safety. Because the prices of the VPNs are high and a user who wants to use this digital tool for one time should not be paying for that. Most Proxies are unsafe, but free and most VPNs are fully safe, but come with a price.
Due to the use of strong encryption of the VPN, the connection speed can go down a little, but it will still be faster than the most proxies. When it comes to choosing proxy or VPN, there are many shady proxies and VPNs out there, so choosing a good one will be necessary for the user.





