What is AggregatorHost.exe? Is it Safe or Harmful?
Most users who found the AggregatorHost.exe in their Task Manager are wondering what this is and is it safe or harmful. Users always get curious when they find an unknown process running in their Task Manager without their knowledge. There is very less knowledge about some processes by Microsoft. In this article, we will provide all the available information related to the AggregatorHost.exe application.
What is AggregatorHost.exe?
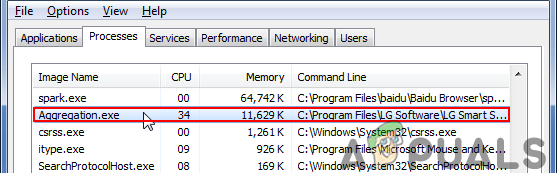
This file is related to Windows and you can find it running in the Task Manager. The file will have no information in the properties window. Some users notice the appearance and disappearance of this process related to the Windows Defender. There are some other similar files named “aggregator.exe” which can be found with Adobe applications or LG Smart Share. Many users mistake these two files, which are mostly located in different locations. The path of the file also gives an idea about what the process can be.
Is AggregatorHost.exe Legit?
The location of this specific file will be the “C:\Windows\System32” folder of your system. The other “aggregator.exe” file will be located in the path of that specific application. It is best to know where the file should be, so you will know if it is legit or not. If it is located in the mentioned paths, then the file is legit and you should not worry about it.
Is it Safe or Harmful?
If the file is located in the correct path, then it isn’t harmful, and we consider it a safe file. For most files, you can find the information through the properties of the file. If it is empty like this one, then you should always check the file path of the process running in the Task Manager. As far as most users found out about this process, there were no harmful things happening to their system.
However, if the file is located somewhere else rather than the correct location. Then you need to run the malware scan on your system to be safe. There can be some malicious file that camouflages itself as this file. It is recommended to use Malwarebytes to scan for any virus and malicious files.