How to Check Who is Connected to Your WiFi Network?
Sometimes the WiFi network without security can be used by anyone within the range of the signal. Too many users on a network will make the Internet slow. Checking who is using your internet and putting security on it will help with the problem. However, many people have very little knowledge about the settings of the router or checking the connected network connections. In this article, we will show you the methods for checking the users that are connected to your WiFi network.
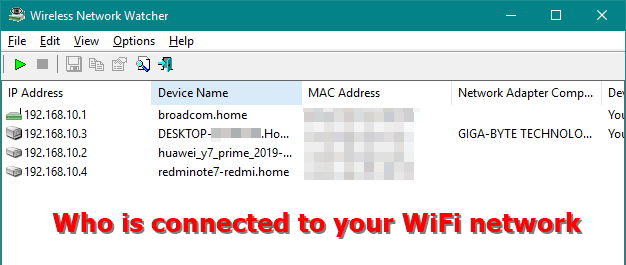
Checking who is connected to Your WiFi Network
There are many reasons for checking the devices that are connected to your WiFi network. Sometimes, some unknown users might be using the internet which can slow down the speed of the internet. It is also not safe when some unknown users are connected to your home network. To take any action against these, the user must see who is connected to their network first. You can easily check the connected devices to your network through these methods.
Method 1: Checking through Internet Router/Modem
This method will depend on the router/modem that the user is using. Each modem/router has a different interface and options. Most of the router’s username and password for logging in will be “admin”. However, some will have a different password that you can find on the back of the router. The same goes for IP address, every router of the different companies will have a different IP address. Most of the time the connected devices can be found in the Status or Information menu of the router. Follow the below steps to get the idea about where to find the connected devices:
- Open a browser, type the IP address of the router and log in to your Router.
Note: Find the IP address, username, and password of the router on the back of your router.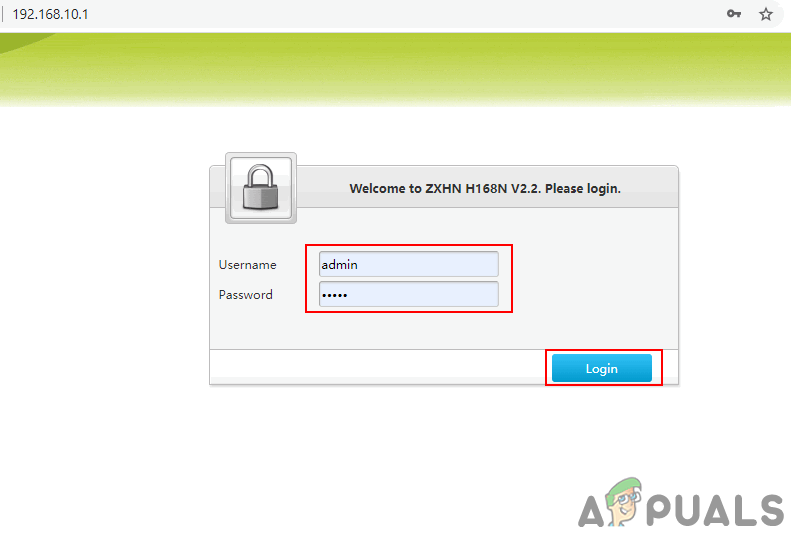
Logging in to the router - The settings will depend on each router, but mostly it can be found in Status or Info of connections. For us, we go to Device info and click on DHCP.
Note: For some users, the option will be wireless clients.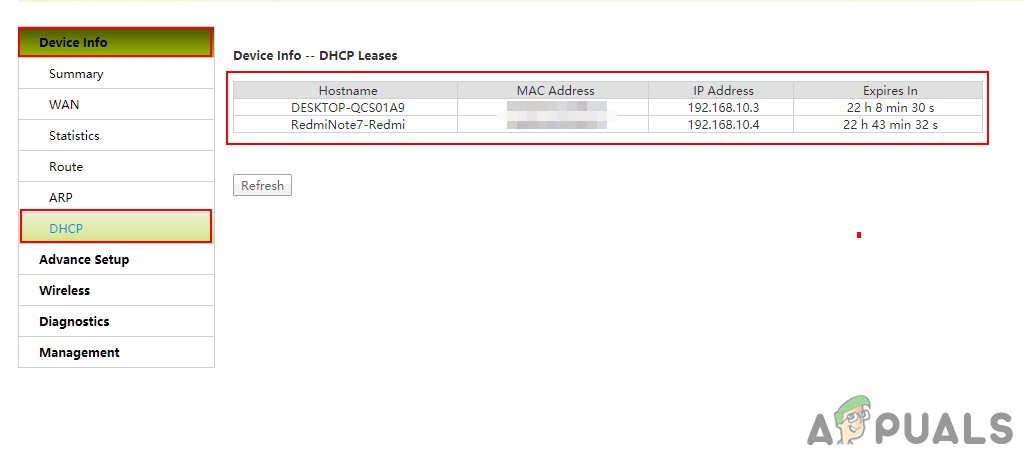
Opening the DHCP option - Here you can see the information about all the devices that are connected to the router.
Method 2: Checking through Third-Party Software
The other method to check the connections is by using the third-party application. There are many third-party applications that can show the connection that is connected to your network. In this method, we will be using the Wireless Network Watcher by Nir Soft. Follow the below steps to download and use the Wireless Network Watcher application.
- Open your browser and download the Wireless Network Watcher application.
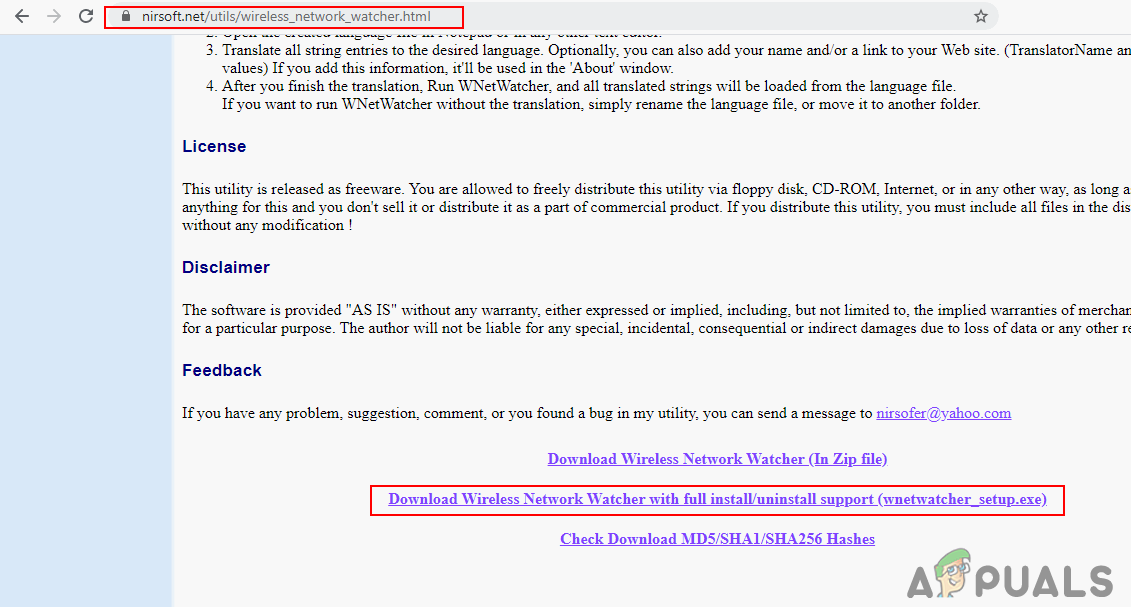
Downloading the Wireless Network Watcher - Install the program by following the installation steps and then open it.
- When you open the application, it will automatically start searching for the connected devices and the router.
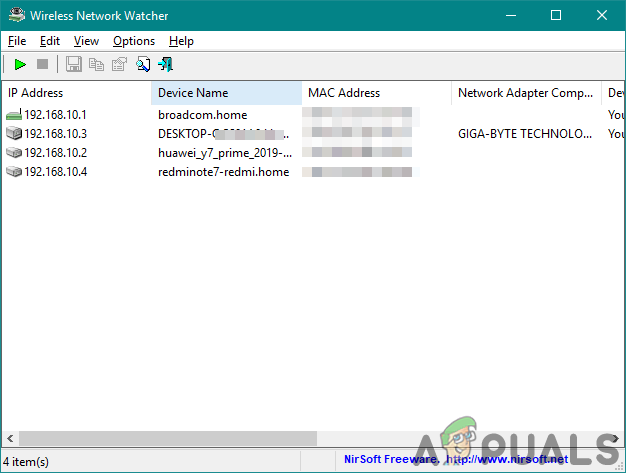
Searching for all the IP addresses - You can get the MAC address and all the other information through this application. It also provides the Play/Stop button for searching again later.
Additional: Blocking Someone from Your Network
This method is for blocking some unknown users from your network. Most router/modem has a setting for MAC filtering that can be used for allowing/blocking users. Every device will have a different MAC address and we can add these addresses in the MAC filtering to allow or block them from the network. Follow the below steps to block someone from Network:
- Open your router IP address in the browser and log in.

Logging in to the router - Go to the Wireless Settings and click on Mac Filter or Mac Filtering option.
Note: Sometimes it can be found in the Advanced wireless settings.
Opening MAC Filtering option in the router - Now here you can add/remove MAC addresses and then choose the option to allow or deny them on your network.
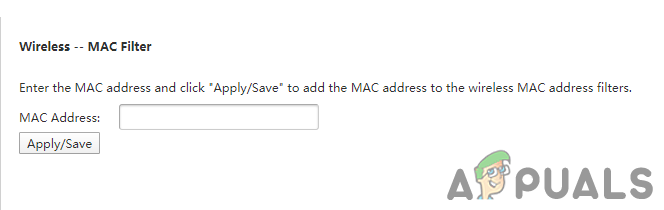
Adding new MAC address into MAC filter - Save the settings and restart your router if needed. This will completely block the users or only allow the users that are on the list.