What is hydra.exe and Should You Delete it?
The legitimate Hydra executable (hydra.exe) is a process belonging to Hotspot Shield. Hotspot Shield is a virtual private network (VPN) utility developed by AnchorFree. It’s frequently used to secure internet connections on unsecured networks – it’s one of the preferred tools to bypass government internet censorship. However, because it filters internet connections and has access to all the data that you exchange over the internet, hydra.exe (belonging to Hotspot Shield) is one of the most preferred targets for cyberpunks that write ill-intended malware.
Some users have been reporting that a certain hydra.exe executable is actively using the internet connection and system resources. This article is meant as an explanation guide, detailing the procedure of identifying if hydra.exe is a virus or a legitimate component and dealing with it.
Potential security risk
As a virus, hydra.exe can be traced all the way back to Windows 93. Back then it was a joke program of sorts that didn’t do any real damage to infected systems. It was nothing more than a joke program that opened a dialog box impossible to close. The dialog box was either a standard error message or contained the text “Cut off a head, two more will take its place”. Every time the user closed one error window, two more clones appeared. There are a lot of variations of this virus, but they all have the same behavior.
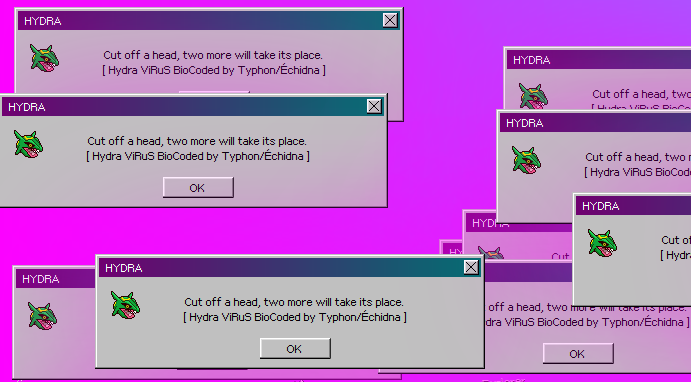
But as stated above, the harmless virus kickstarted from an executable and could be stopped with a simple OS restart. Even more, heightened security protocols made it impossible for the joke virus to be recreated on ulterior Windows versions.
However, this harmless virus gave birth to something much more severe. Over the past 10 years, malware creators borrowed the famous name and used it for a wide range of powerful hacking tools. Nowadays there are a lot of viruses and hacking tools that are named or contain the name Hydra. In 2017, the focus was on a very scary fast network logon cracker that was used effectively throughout the year to break millions of passwords by deploying a suite of innovative attack protocols on vulnerable PCs.
On top of this, the legitimate Hydra (hydra.exe) executable (belonging to Hotspot Shield) is a prized target for any respectable malware. The new batch of trojan variations that are known to target executables with enhanced privileges are often variations of crypto-trojans. These trojans often get spread by p2p file sharing, spam emails or chained installations. Once it gains entry to your system, the virus camouflages itself into a file with elevated privileges – preferably with access to your personal data. As you can imagine, there are few better targets than an executable that filters the internet connection (hydra.exe). Once the virus is in place, it will start to mine personal data/bank account information or lay the grounds for a future Crypto-Trojan attack.
Determining if hydra.exe is a virus
In order to determine if you’re dealing with the virus, think long and hard if you ever used Hotspot Shield to connect to a VPN network. If the answer is no, then it makes no sense for you to have an active hydra.exe process in your Task Manager that is actively using your system resources.
But as with most viruses, the most effective method of determining if a certain file is infected is to view its location. To do this, pop open Resource Monitor or Task Manager (Ctrl + Shift + Esc) and find the hydra.exe executable in your Processes list. Then, right-click on the hydra.exe process and choose Open File Location.
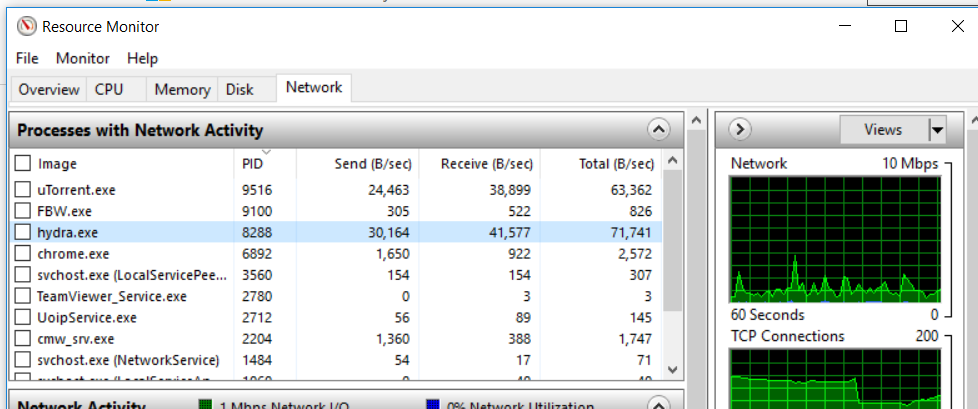
If the revealed location is anywhere else than C:\ Program Files \ Hotspot Shield \ bin \, you are probably dealing with a virus infection. In the event that the location is the same as the one mentioned above, check to see if you have Hotspot Shield installed. The software has a lot of traction with some PC components manufacturers and might have been bundled with certain drivers, without you specifically installing it.
Note: Even if you determined that hydra.exe is in the default location, it’s advisable that you still follow the steps in the last paragraph to make sure that your system does not have a security vulnerability.
Should I remove hydra.exe?
This decision is highly dependent on the above outcome. If you previously determined that you’re dealing with a virus, you absolutely need to deal with the security threat. In the event that hydra.exe hasn’t gone rogue, it’s up to you if you want to remove it or not. Keep in mind that hydra.exe is not a Windows core process, and deleting the executable will not affect your system functionality in any other way than interrupting your VPN connection – if you’re actively using one through Hotspot Shield.
In the event that you’re not using a VPN connection via hydra.exe, it doesn’t really make sense to keep Hotspot Shield installed on your system. The program has a background process that is configured to run at startup and will use system resources regardless if you’re using Hotspot Shield or not.
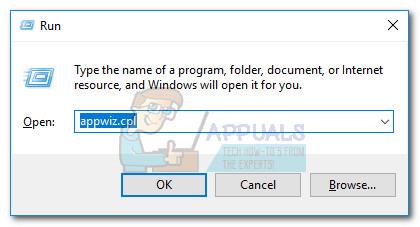
If you decide to remove the executable, do not delete just hydra.exe. Instead, uninstall the whole Hootsuite Shield program via uninstall.exe (C:\ Program Files \ Hotspot Shield \ bin \ uninstall.exe) or open a Run window (Windows key + R), type “appwiz.cpl” and uninstall Hotspot Shield from the Programs and features list.
Dealing with a security threat
If the location of hydra.exe was anywhere else that the location mentioned or if the executable got flagged by your security suite, you need to take the steps necessary to remove the threat. For the best results, we recommend scanning your system with Malware Bytes. If you’re having trouble using it, follow our in-depth guide (remove malwares) to use it effectively. Additionally, you can use Microsoft’s Safety Scanner (here) to reverse the changes made by the identified threats.
Important: If the scan has revealed the virus Hacktool.Hydra (hydra.exe) or a similar name, think back if you ever used any banking information on this computer. If you did, you need to assume that the information has already been compromised, because this is exactly what the Hacktool.Hydra virus is after. In such a case, contact any banks or eCommerce sites you might have recently used and let them know that unauthorized individuals might have access to your account. Also, blocking recurrent payments from your bank account a good idea at this point.