How to Remove Fake Tech Support Number from Taskbar
There are numerous instances where people get targeted by Trojans by downloading applications over the internet. A Trojan horse is a kind of malware. It is a special program which pretends to be useful for your computer but isn’t in reality.
It is very rare to a Trojan to be on your computer by just visiting a website. They are usually attached with different applications such as wallpapers, music, games, backgrounds, and PC optimization software etc.
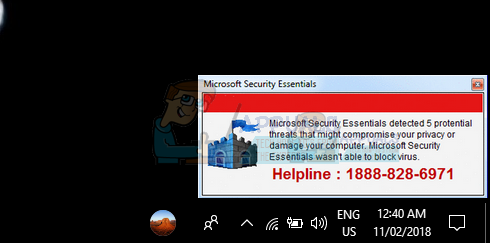
You might get different pop-ups on your screen stating that your PC was detected having a potential risk or some error condition which happened recently will be displayed on the screen. All of them are fake and mean nothing in particular. They are meant to make you believe something is wrong so you can call the helpline or click the link and get scammed.
How to Remove the Scam Completely?
There are a number of steps which you have to perform in order to completely eradicate the Trojan/malware from your computer. Do note that the Trojan would be hidden from plain sight and you will have to scan your computer thoroughly to remove it.
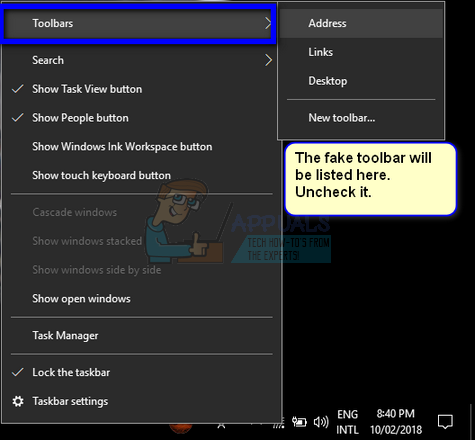
Before we begin with the steps to remove it completely, we will first disable it from your taskbar. Right-click your taskbar so all the list of options pops up. Select Toolbars and uncheck all the entries. Even though you may be using some of them, it is wise to disable all of them to cancel the possibility of any part being ignored.
Now navigate to How to remove fake tech support from your computer. We have written a detailed explanation with pictorial representation on how to remove it completely from your computer. We have also explained all the mechanics involved in the process.
Here is a list of what you will be doing just in advance:
- Remove the Trojan/malware using the control panel.
- Running AdwCleaner and scanning your computer.
- Running Malwarebytes and scanning your computer.
- Running Hitman Pro and scanning your computer.
- Clearing all the cookies and irrelevant extensions from your computer so no remnants are left behind.
After you are done with all the steps explained in the link above, your PC will be clean from all the threats. In very extreme rare cases you have to resort to installing a new copy of Windows using an ISO disk file but it won’t come to that in our case.