Unable to delete a suspicious file in Windows? – Try this!
In this article, we will explore the various reasons why you might encounter errors and difficulties when trying to delete suspicious files and folders in Windows and provide effective methods to delete them.
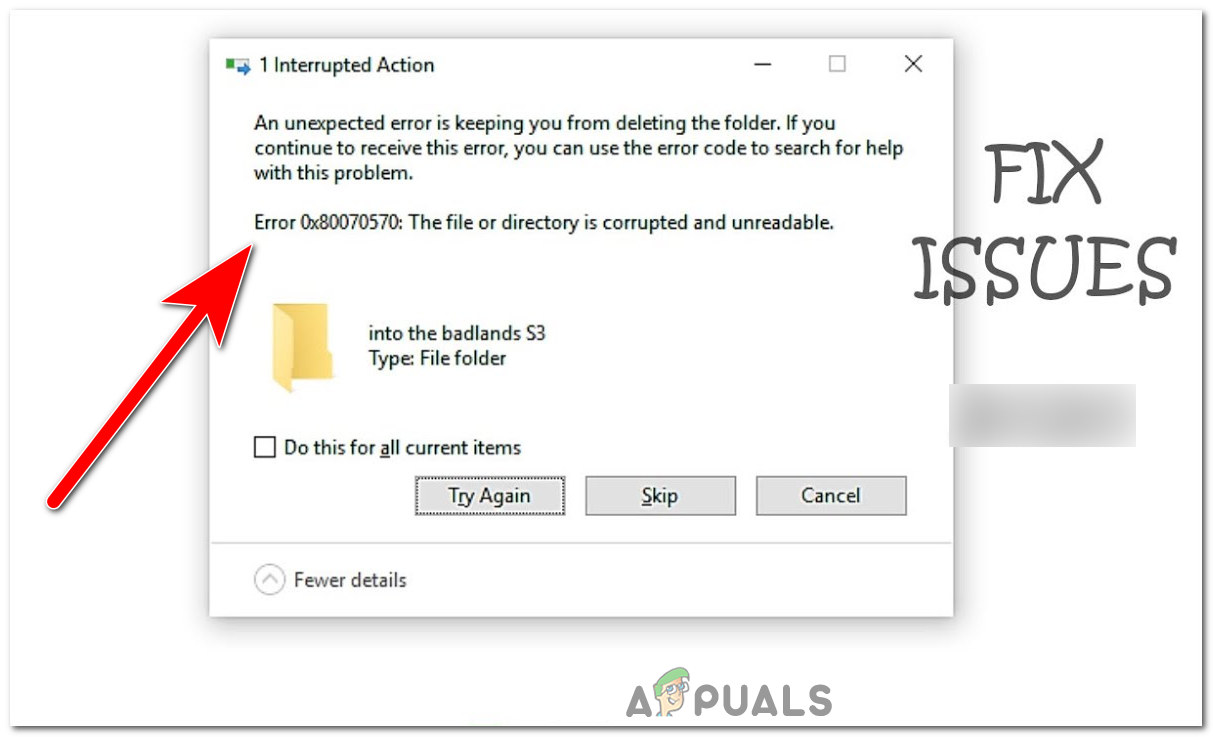
Suspicious files are potential threats to your computer’s security and they can even contain malware or harmful content. It is important to handle such infected files with caution and follow proper procedures to ensure the safety of your device.
What are Suspicious Files?
Suspicious files are files that raise concerns due to their unknown origin, unusual behavior, or association with potentially harmful activities. These files may be detected by antivirus software or identified manually based on their filenames, extensions, or locations.
How Do Suspicious Files End up on My Computer?
These files can find their way onto your computer through various means, including:
- Downloads from Untrusted Sources: Downloading files from unverified websites or peer to peer networks can expose your system to potential threats.
- Email Attachments: Opening email attachments from unknown senders can lead to the infiltration of these infected files.
- Infected External Devices: Connecting infected USB drives or external storage devices can also cause this.
The Challenges of Deleting Suspicious Files
These types of files have different techniques that are implemented by the hacker, which causes challenges while deleting them. Some of these techniques are stated below:
- File Locking: One common reason you might face difficulties deleting suspicious files is that they are in use or locked by a running process. Some malware or programs may keep a file locked to prevent their removal.
- Insufficient Permissions: If you keep encountering the “Access Denied” error while trying to delete these files, it is due to insufficient permissions. Certain infected files may require administrator privileges for deletion.
- Hidden and System Files: Suspicious files can be hidden or marked as system files, making them harder to locate and delete manually.
- Self Replicating Malware: In some cases, suspicious files might be part of self replicating malware, making it challenging to eliminate them entirely without proper removal tools.
How to Delete Suspicious Files?
Deleting these files can sometimes become a chore due to the techniques implemented by hackers. However, we have conceived the best solutions and tested them on malware with great success. Here are all the ways to eradicate these files in a matter of minutes:
- Use an Antivirus Software: The best way to find and delete infected files from your computer is by using an antivirus software. Antivirus programs are made to find and get rid of malware, as well as these infected files that could harm your system. You can use Windows in house antivirus to scan and delete these Suspicious Files, and it’s free.
- Boot into Safe Mode: Booting your Windows computer into Safe Mode allows you to start your system with minimal drivers and only essential processes running. This will help in dealing with thus files that may be actively in use or protected by certain processes in normal mode. By doing this, you have a better chance of successfully deleting these files.
- Take Ownership of the File: Taking ownership of a file allows you to gain full control and permissions over it. This is particularly useful when dealing with files that are protected by certain processes or, when encountering the “Access Denied” error during deletion. By taking ownership of the file, you can bypass these permission restrictions and ensure the ability to delete the file.
- Use Command Prompt: Using Command Prompt in Windows can be a powerful way to handle files, that may be difficult to delete through the regular graphical interface. Command Prompt provides more direct access to file operations, and by running it with administrative privileges, you can bypass certain restrictions that may be interfering.
1. Use an Antivirus Software
- Click on the Windows + I key to open Windows Settings.
- In the Settings window, click on “Update & Security.”
- In the left sidebar of the Update & Security window, click on “Windows Security”, and then “Open Windows Security”.
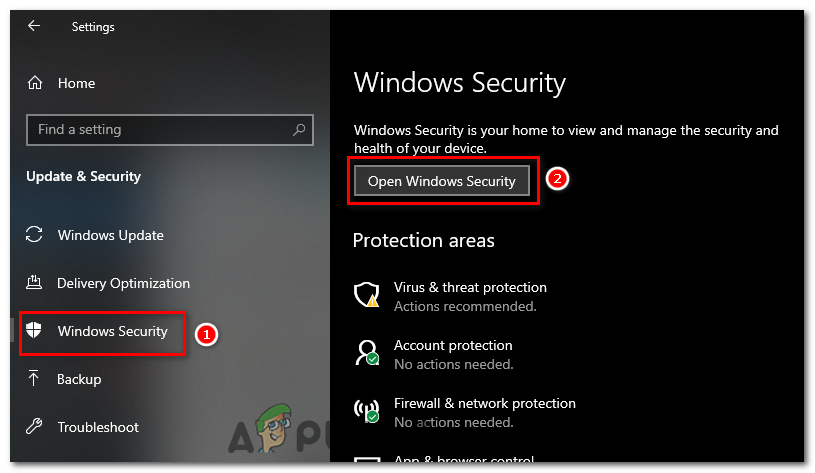
Select Windows Security in the left tab and click on the Open Windows Security button. - Within the Windows Security application, click on “Virus & Threat Protection” in the left menu.
- Under the “Quick Scan” section, click on the “Quick Scan” button. This will perform a rapid scan for the most critical areas of your computer.
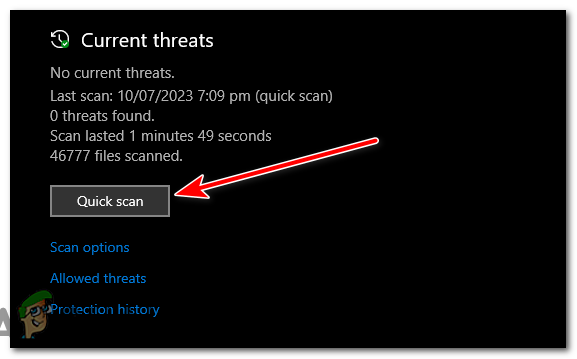
Click on the “Quick Scan” button. - After the quick scan is completed, the results will be displayed. If any suspicious files are detected, Windows Security will prompt you to take appropriate actions.
- Perform a Full Scan (Optional): If the quick scan does not detect the suspicious files or you want a more comprehensive scan, you can run a full scan. Scroll down to the “Scan options” section and click on “Full Scan.”
- Click on the “Scan Now” button under the “Full Scan” option. Windows Security will now scan your entire system thoroughly for any potential threats.
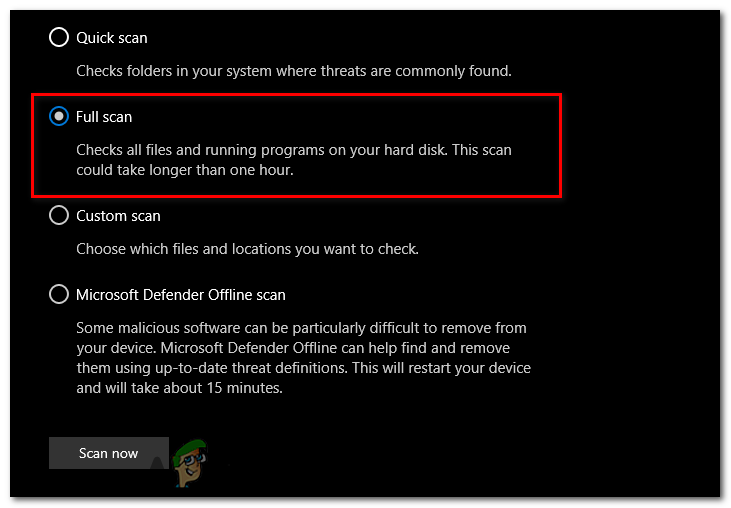
Click on the “Scan Now” button under the “Full Scan” option. - Once the full scan is finished, you will see the scan results. If any files are detected as malware, Windows Security will suggest actions to be taken.
- Windows Security will provide the options “Quarantine” and “Remove”. Select “Remove”.
- In some cases, Windows Security will need your confirmation before taking action on a suspicious file. So press YES if prompted for administrator privileges.
2. Boot into Safe Mode
Before proceeding, make sure to save any important work you have open and close all running applications. Booting into Safe Mode will temporarily stop all non essential processes. To access the Advanced Startup options and boot into safe mode, follow these steps:
- Click on the Start button, then click on the Power icon. While holding down the Shift key on your keyboard, click on “Restart.”
- Select Troubleshoot.
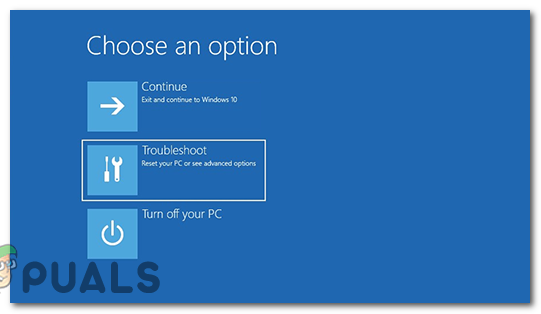
Click on Troubleshoot. - Now select “Advanced options.”
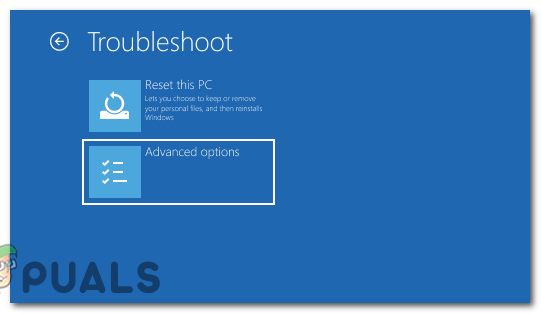
select “Advanced options.” - Under Advanced options, click on “Startup Settings.”
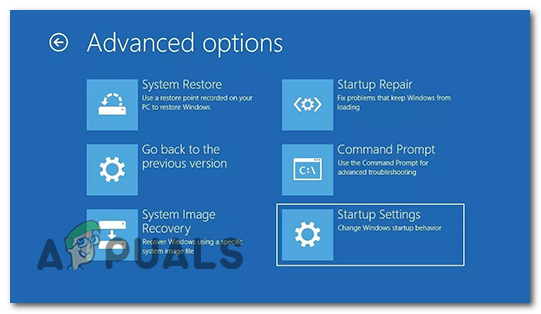
Click on “Startup Settings.” - You will see a list of startup options. Press the corresponding number key to “Enable Safe Mode.” If you need internet access while in Safe Mode, you can choose Safe Mode with Networking.
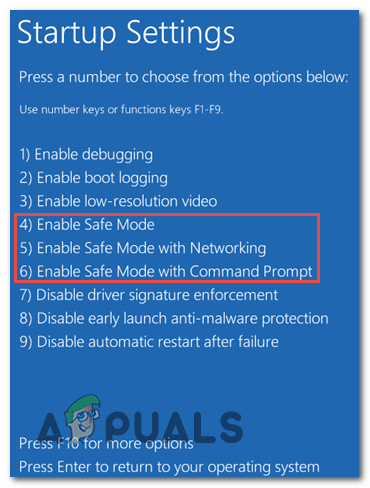
Press the corresponding number key to “Enable Safe Mode.” - Your computer will now restart and boot into Safe Mode. You will see “Safe Mode” displayed in the corners of the screen, indicating that you are in this mode.
- Once you are in Safe Mode, navigate to the location of the file you want to delete.
- Right click on the file and select “Delete” from the context menu.
- After you have successfully deleted the file, restart your computer to exit Safe Mode and boot back into normal mode.
Note: Safe Mode is designed to be a diagnostic environment, so some features and drivers will not be available. Use Safe Mode only when necessary for troubleshooting purposes, and exercise caution while deleting files to avoid accidental deletion of important data.
3. Take Ownership of the File
- Before taking ownership of the file, locate its location on your computer.
- Once you have found the file, right click on it to open the context menu.
- From the context menu, click on “Properties” at the bottom.
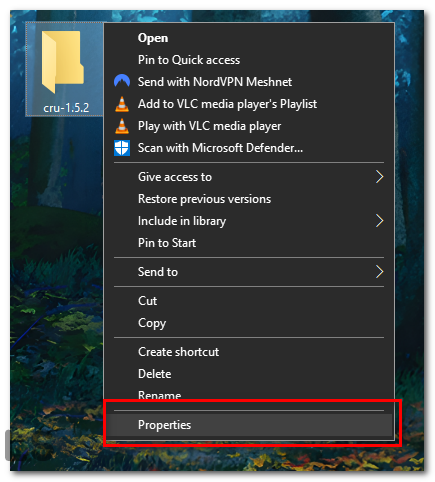
Right click on the file, and click on “Properties” at the bottom. - Once the properties window has opened. Click on the “Security” tab.
- At the bottom of the “Security” tab window, you will see an “Advanced” button. Click on it.
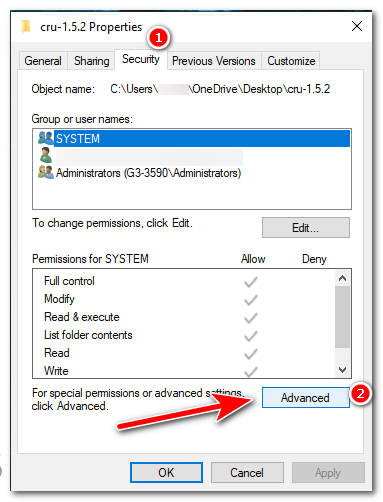
In the “Security” tab window, press the “Advanced” button. - At the top of the “Advanced Security Settings” window, you will also see the name of the current owner. Next to this, click on the “Change” link.
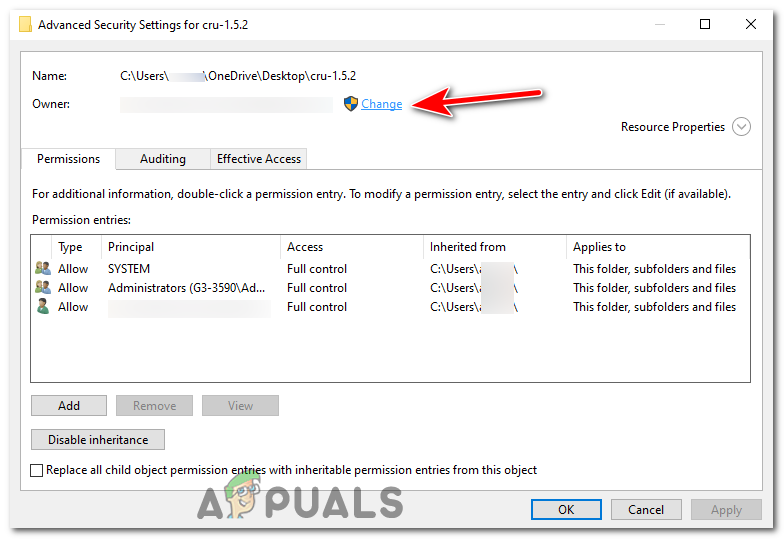
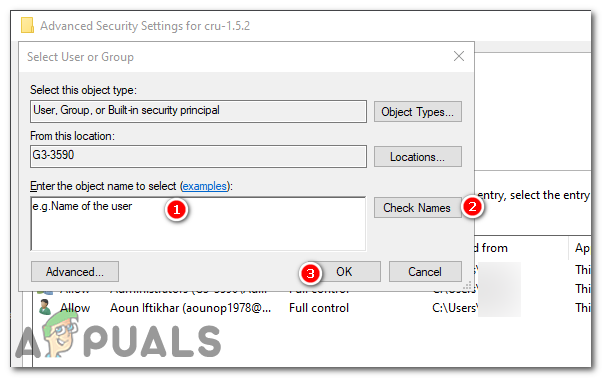
In the “Security” tab window,press the “Advanced” button. - In the “Select User or Group” window that opens, there is an empty text box. Here, you have to type your username.
- Click on the “Check Names” button next to the text box. Your computer will verify whether the username you entered exists. If it does, the text you entered will change to show the correct object name.
- Once you have verified your username, click on “OK”. you will be brought back to the “Advanced Security Settings” window.
 Change Permissions (Optional): If you also need to modify the permissions of the file or folder, under the “Permission entries” box, click “Add”. Then click “Select a principal” and add your user name again. You can then select the permissions you need (Full control, Modify, Read & execute, etc.). Click “OK” when you’re done.
Change Permissions (Optional): If you also need to modify the permissions of the file or folder, under the “Permission entries” box, click “Add”. Then click “Select a principal” and add your user name again. You can then select the permissions you need (Full control, Modify, Read & execute, etc.). Click “OK” when you’re done.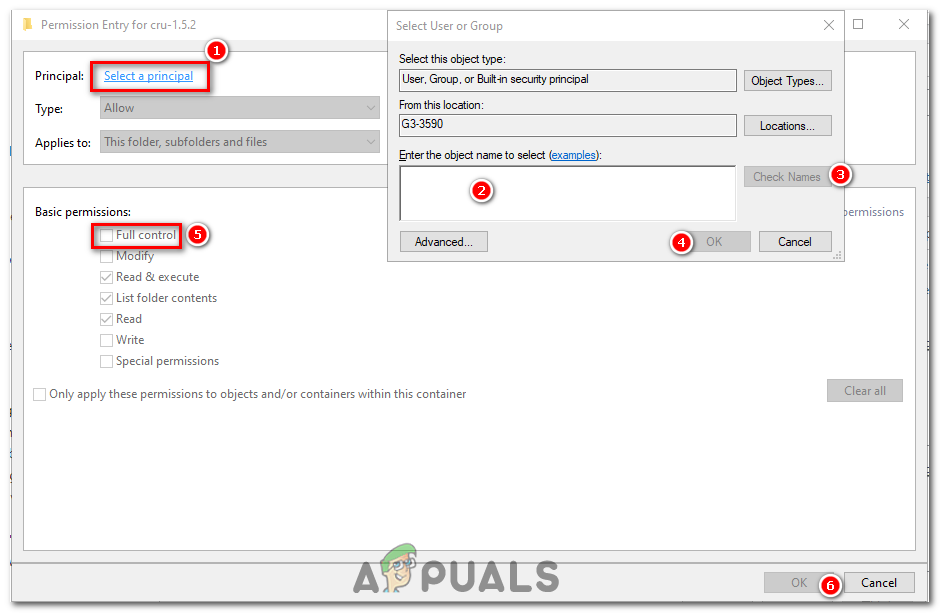
- If you are taking ownership of a folder, you may also want to take ownership of all files and subfolders within it. If so, check the box next to “Replaceowner on subcontainers and objects” before proceeding.
- Once you have made all your changes, click on the “Apply” button at the bottom right of the window.
- A pop up window will appear asking if you are sure that you want to make these changes. Click “Yes”.
- Click “OK” on all open properties windows to close them and finish the process. Your changes will now be applied.
- Now that you have taken ownership of the suspicious file, try deleting it again and see if it works.
4. Use Command Prompt
Note: Exercise caution and ensure that you are deleting the correct file to avoid unintended consequences. If you are uncertain about the file’s legitimacy, perform a thorough scan with an antivirus software before proceeding with the deletion.
- Press the Windows key + S to open Windows search. Type “CMD” and right click on it, select “run as administrator”.
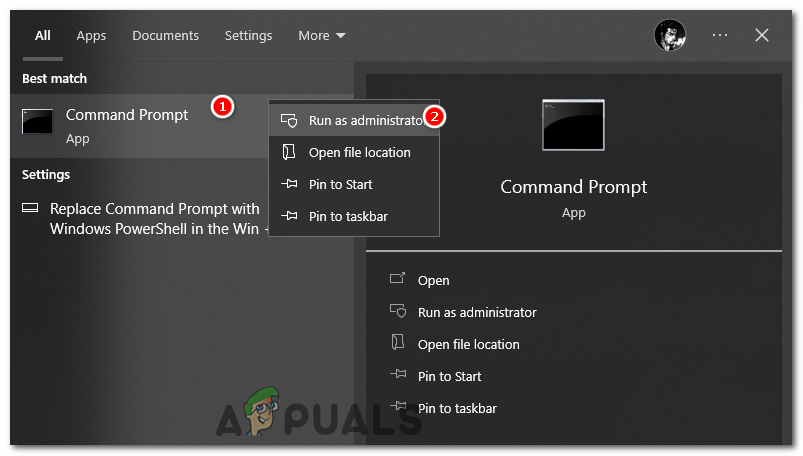
Open Command Prompt as administrator. - In the Command Prompt, you will start in the default directory (usually C:\Windows\system32). If the suspicious file is located in a different directory, use the cd command to change to that directory. For example, to change to the Desktop directory, type: cd “Desktop file path” and press Enter.
cd "C:\Users\username\OneDrive\Desktop"
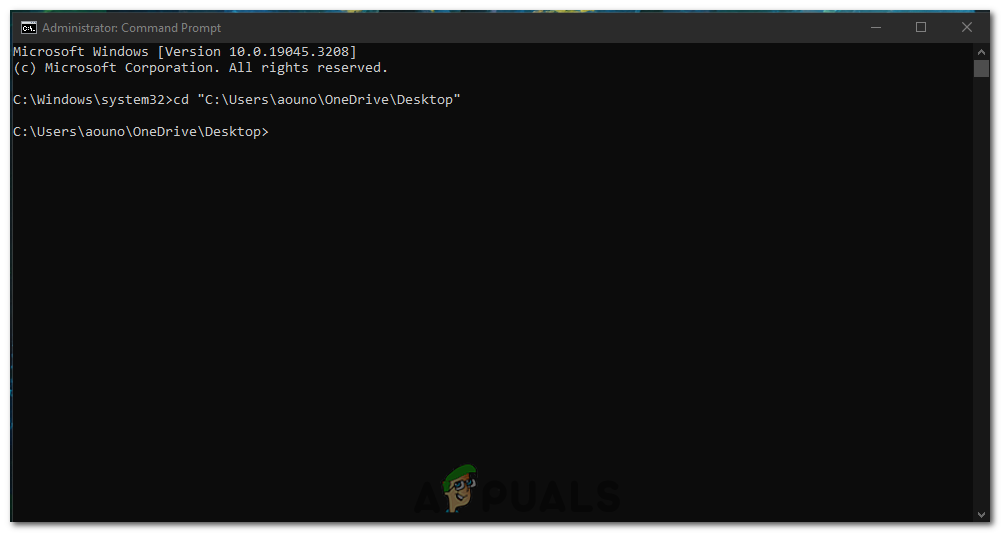
Open the directory of the folder where the file is located. - To verify that you are in the correct directory, type dir and press Enter. This command will display a list of files and folders in the current directory.
dir
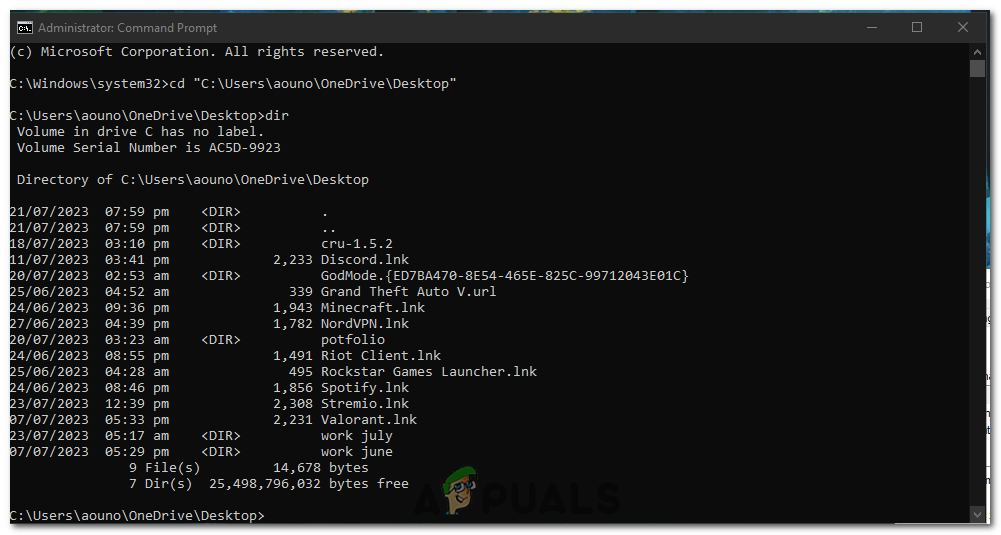
Use the dir command to verify if its the right directory. - Scan the list of files displayed by the dir command and locate the file you want to delete. Note its exact filename and extension.
- To delete the suspicious file, type the following command and press Enter:
del filename
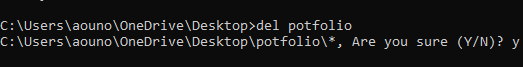
Use the dir command to verify if its the right directory. - Replace filename with the actual name of the suspicious file. For example, if the suspicious file is named “example.exe,” the command will be:
del example.exe
- After executing the del command, the Command Prompt will ask for confirmation. Type “Y” and press Enter to confirm the deletion.
- After the deletion process is complete, Command Prompt will display a message confirming the action. To ensure that the file has been successfully deleted, use the dir command again to check if the file is no longer listed.
- Once you have confirmed that the file has been deleted. Type exit and press Enter to simply close the Command Prompt window.
5. Reinstall Windows
If nothing seems to be working for you, reinstalling Windows might be the only way to get rid of these Suspicious files. This approach will essentially wipe your system clean and reinstall the operating system, remove all files and programs, including the infected ones.
But before proceeding with this fix, make sure to back up your important data, as reinstalling Windows will result in the loss of all data and installed applications. Luckily, we have a well detailed guide on How to Reinstall Windows on our website, so you can follow that along and do it.
Precautions you can take to Prevent Infection in the Future
Since these attacks have become common nowadays, you should be catious about them. These are the precautions you should take to prevent from further attacks in the future by these suspicious files:
- Keeping your Operating System Updated: Regularly updating your operating system patches security vulnerabilities and enhances your computer’s resistance against threats.
- Installing a Reliable Antivirus: A reliable antivirus program is your first line of defense against suspicious files. It detects, quarantines, and eliminates threats before they can cause harm.
- Regularly Scanning Your System: Even with an antivirus, some threats might slip through. Regular system scans can help detect and remove them.
- Be Wary of Suspicious Emails and Websites: Always exercise caution when clicking on links or downloading files from emails or websites. If something seems off, it is best to avoid it.
- Regularly Backing Up Your Data: In case your computer gets infected, having a backup of your data can save you from losing valuable information.
Why Cannot I Delete Suspicious File in Windows - FAQs
No, deleting system files can cause serious issues with your operating system. Only delete files if you are certain they are malicious.
While manual deletion is possible, using an antivirus software ensures a more thorough and safer removal process.
There isn’t a one size fits all answer to this, as the best antivirus depends on your specific needs. However, some well regarded options include Fortect, Norton, Bitdefender, and McAfee.
In some cases, you may recover deleted files from your Recycle Bin or using data recovery software. However, it’s not guaranteed.
Phishing emails or websites often have spelling mistakes, ask for personal information, and have a sense of urgency. Always double check the sender’s email address and the URL of the website.
 Reviewed by
Reviewed by 




