How to Tell If Your Phone is Tapped – Guide to Stay Safe
Hackers may use a mobile network or specialized software (often via mobile apps) to track your location and monitor your conversations—an activity known as phone tapping. As spyware technology becomes more advanced, it remains possible for mobile users to have their phones tapped without realizing it. While occasional phone issues are common, persistent unusual symptoms may indicate your device has been compromised.
Let’s explore these signs and learn how to spot issues early so you can protect yourself before anything critical occurs. Even if your device has already been compromised, you can take meaningful steps to regain control by following our comprehensive post-hack guide.
Decreased Battery Capacity

A compromised (or “bugged”) phone often experiences decreased battery life. If someone is tapping your phone, they may be listening to your conversations and transmitting that information elsewhere. This covert activity places a constant drain on your battery, leaving a clear physical sign on the device.
Malicious software can even record audio in your environment without your knowledge, significantly increasing battery consumption—even when your phone appears to be idle.
To verify this issue, try using your battery in another device of the same model. Compare how quickly your phone requires charging against other devices with the same hardware and operating system. If your phone’s battery depletes much faster than comparable devices, this could indicate malfunction or hacking activity.
Check Battery Usage on Android
- Open your Android device’s settings menu.
Open Settings - Select “Battery” from the settings options.
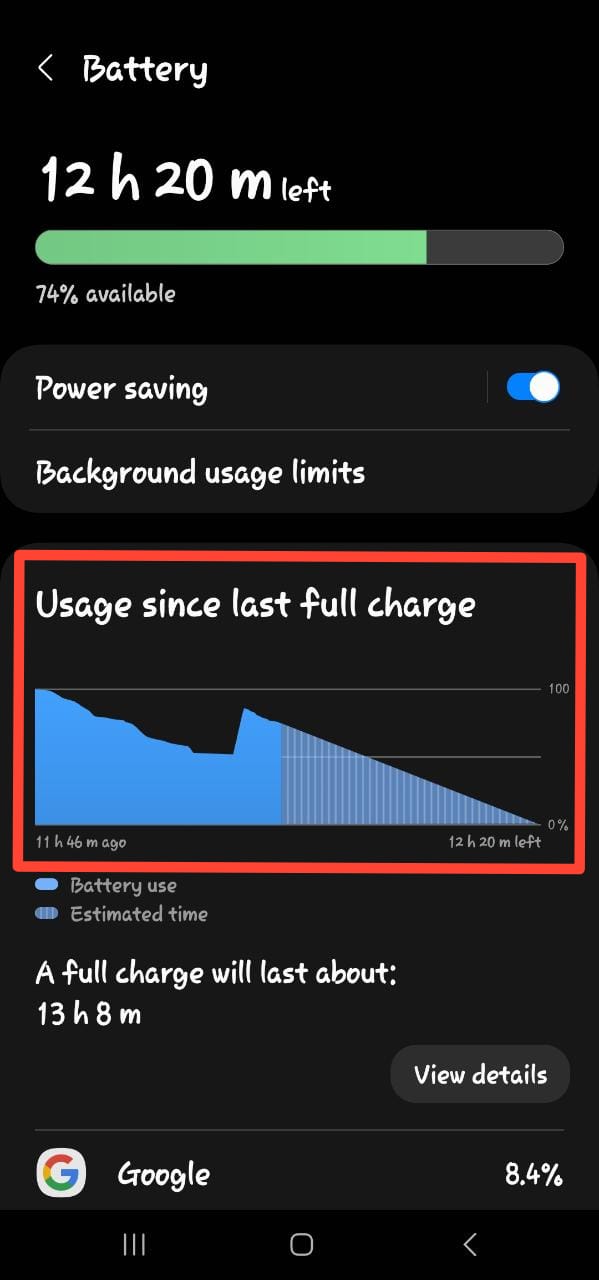
Battery and Device Care - Tap “View Detailed Usage” to see which applications are consuming the most battery.
Battery Usage
Check Battery Usage on iPhone
- Open your iPhone system settings.
- Tap the “Battery” option.
- Scroll down to review battery usage by app and recent activity.
Your Camera or Microphone Turns On at Random
Unexpected activation of your camera or microphone is a strong indicator that your phone may be tapped. Devices vary in how they notify users about active camera or microphone usage:
- On an iPhone, a green dot at the top of the screen indicates the camera is active, while an orange dot signifies the microphone is in use.
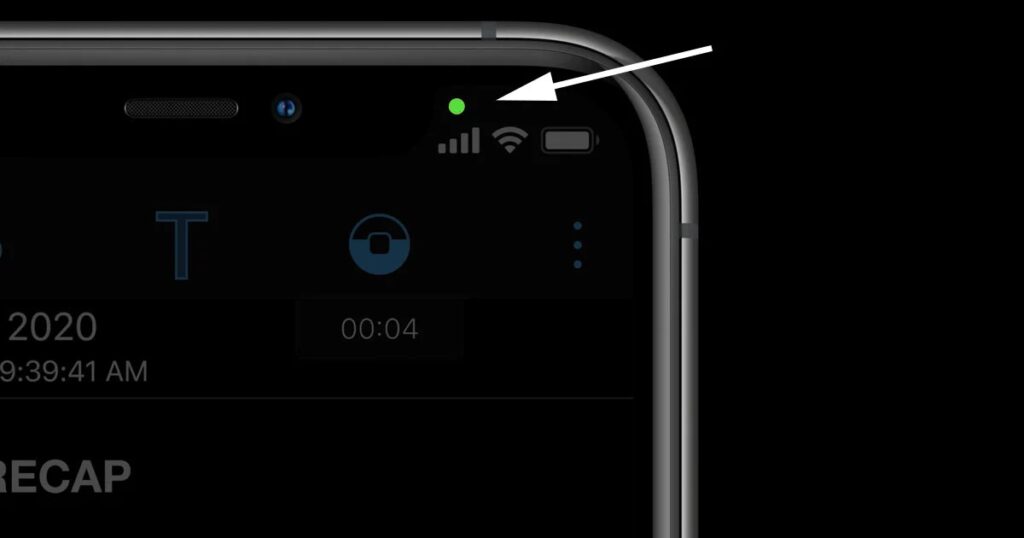
- On Android 12 and newer, a green icon appears in the top-right corner when the camera or microphone is in use.
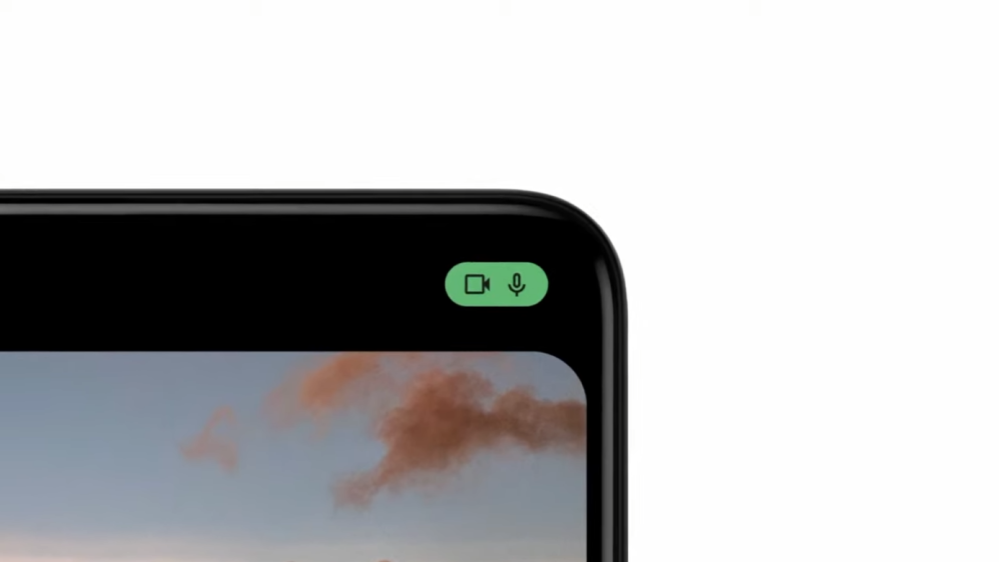
However, the absence of these signs does not guarantee your device is not recording. Unless your phone features a notification light or system alert, it is still possible for spyware to capture audio or video covertly.
If you suspect a hidden camera is monitoring you, our guide on detecting hidden cameras using your phone provides further assistance.
Unusual Background Noise

Strange background noises such as buzzing static, high-pitched vibrations, or unexplained beeps during calls can suggest your phone is being tapped. If you hear these noises, especially when not actively making or receiving calls, your device may be under surveillance. While occasional interference can be normal on both cell and landline calls, frequent or persistent sounds should not be ignored.
You can use your phone’s sound sensor, set to detect low frequencies, to identify noises inaudible to the human ear. Certain apps can function as sound-bandwidth sensors, helping to determine if your device is being monitored. If such an app detects unexplained signals repeatedly, your device may be compromised.
Unusual Pop-Up Ads Appear, Online and Offline

Unwanted pop-up ads frequently signal that your phone has been compromised. Malicious software can cause constant pop-up advertisements—sometimes even outside your browser—on your mobile device. For your privacy and safety, it is critical not to click on these ads or attempt to verify them by following any links they contain.
Many users inadvertently install adware, which floods their phones with intrusive ads without consent. While Android devices are more vulnerable to such malware, iPhones are not immune. To address this risk, consider installing a reputable ad-blocker extension—AdBlock Plus is one such solution that lets you whitelist trusted sites as needed.
Remember, even if the hacker’s primary goal is to display ads for profit, this software can also gather sensitive information and degrade your phone’s performance.
Number To Dial / Code To Check If Your Phone Is Tapped

Certain phone codes can reveal whether your calls, messages, or data are being diverted. Entering these codes lets you see if your line is being redirected—potentially alerting you to unauthorized access or monitoring.
*#21#
Dial *#21# to check the current diversion status on your phone. This code will show if your calls or text messages are being forwarded, which can indicate phone tapping.
*#62#
Dial *#62# to determine whether your calls, texts, and data are being redirected when your device is unavailable or not reachable. Any unexpected results might signal monitoring or unauthorized forwarding.
Websites Don’t Look the Same

Always stay alert to possible fraud attempts. Anyone can make a mistake, such as clicking a suspicious link in an email or text, which can compromise your device. This risk is higher with generic email domains compared to custom domains.
Hackers can also install malicious apps on your phone that alter the appearance of frequently visited websites, even without triggering a link in a message.
Such malicious software can act as a proxy—intercepting your activity, redirecting you to fake sites, or secretly recording your keystrokes to steal personal information. Even using incognito mode or clearing your browsing history will not prevent this risk.
The consequences are especially severe when accessing private accounts or using banking services. Any form of personally identifiable information (PII), such as passwords or account details, can be exposed in this way.
Visual changes on websites—such as unusual layouts, altered logos, or unfamiliar login screens—may be subtle and easy to overlook. Bear in mind, however, that some differences may simply result from responsive themes or updates to the site’s user interface, particularly when switching between mobile and desktop views.
Over-the-Top Data Usage
Even if you are a light data user, regularly check your phone bill and monitor your mobile data usage. Unknown or unexplained spikes in data consumption could suggest your phone is transmitting information in the background—an indicator that your device may be tapped or compromised by spyware.
Check Data Usage on Android
- Go to your Android device’s settings menu.
- Open the “Wi-Fi and Network Settings”.
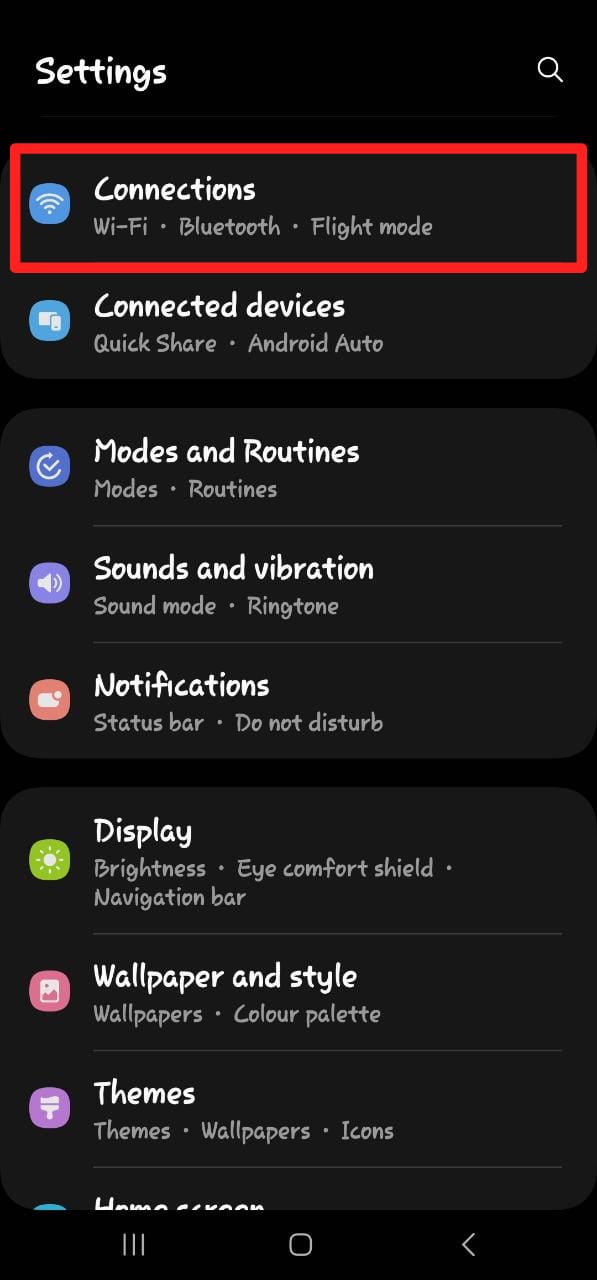
Wi-Fi and Connections - Navigate to Settings > Data Usage to review how much mobile and wireless data you have used.
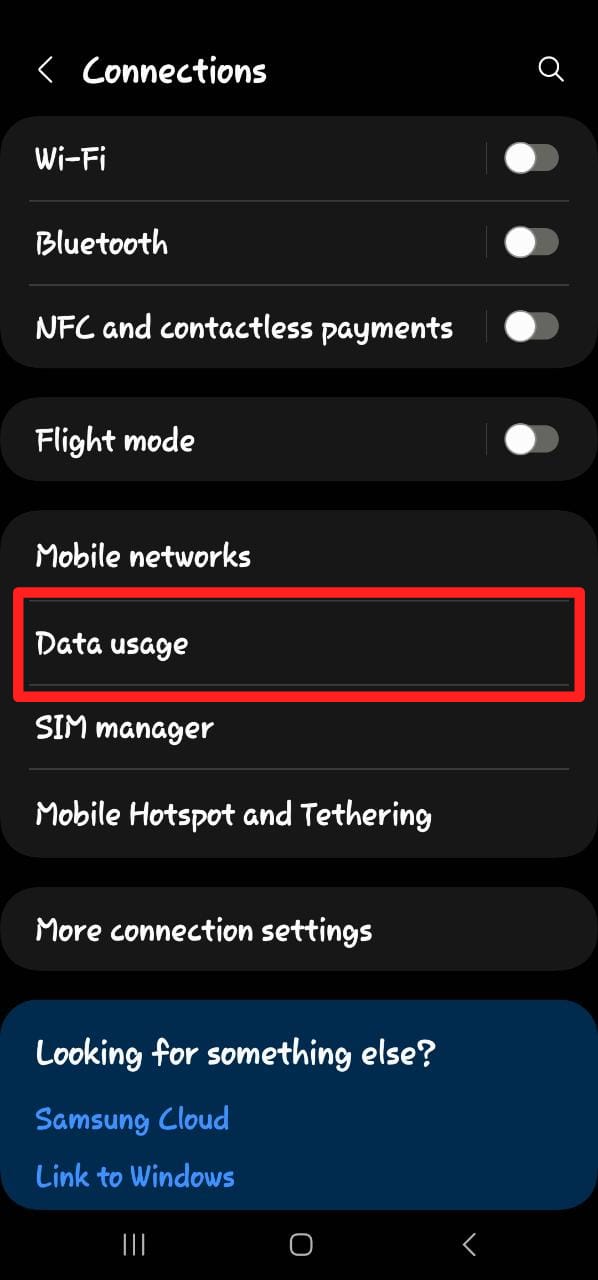
Data Usage
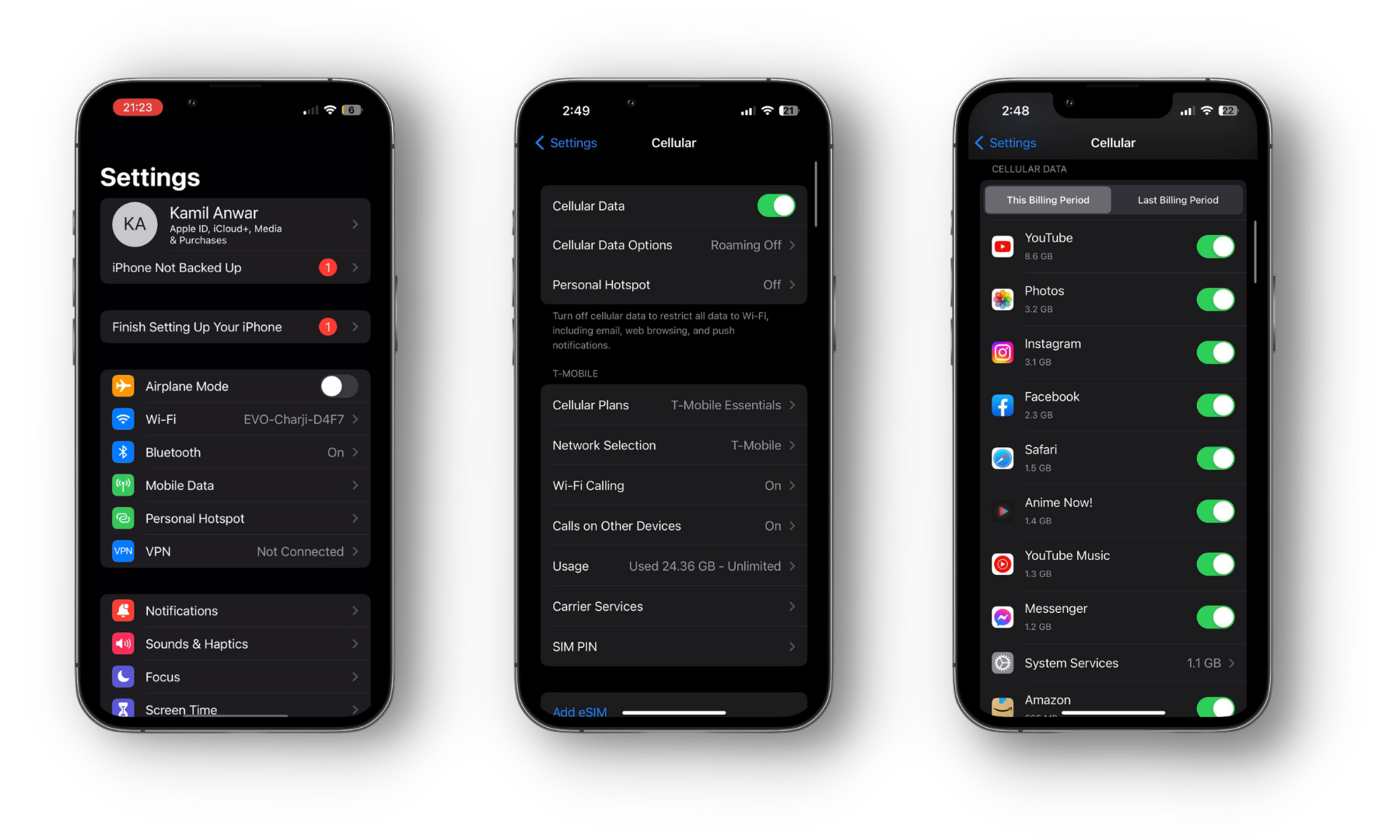
Check Data Usage on iPhone
- Open the Settings app.
- Select “Cellular” (or “Mobile Data”) from the menu.
- Scroll down to view a breakdown of your data usage by app.
- On iOS 15 or earlier, this appears under the “Current Period” section; on iOS 16 and above, look under “This Billing Period“.
Unknown Ads and Apps
It’s easy to overlook forgotten apps on your device, but it’s crucial to stay aware of all installed applications. Unknown or recently installed apps can contain malware or spyware, putting your personal information at risk.
Contrary to popular belief, you don’t need to jailbreak your phone to accidentally download malicious or fake apps. Even the official App Store has occasionally hosted fraudulent apps that may install malware or harvest your private data.
Some malicious ads can trick you into clicking links that lead to payment requests or other threats. Always avoid clicking unfamiliar links, and periodically review your installed apps to ensure your device’s safety and integrity.
 Reviewed by
Reviewed by 




