How to Remove Malware from MacOS
Before starting the “removing” part, make sure you note your Mac’s symptoms and compare with the ones explained here – characteristic for malware and more particularly for DownLite trojan.
Malware (malicious apps) add a browser helper objects in Safari, Firefox, and Chrome. While doing so, they do NOT request permission from the administrator. They also change browsers’ preferences such as homepage and default search engine. Furthermore, they may display advertisements whenever you go to your every-day regular websites, search engines, or e-commerce sites. DownLite trojan particularly makes you visit this site search.conduit.com.
Note: Before performing any of the following steps I highly recommend backing up your Mac’s data.
Method #1 Remove Malware with Malwarebytes
Step #1: Reset Browsers
First, reset your Internet browsers’ settings.
- For Safari
- On the Safari menu bar, click on Safari and choose Reset Safari. Now, make sure you select all boxes, and click Reset.
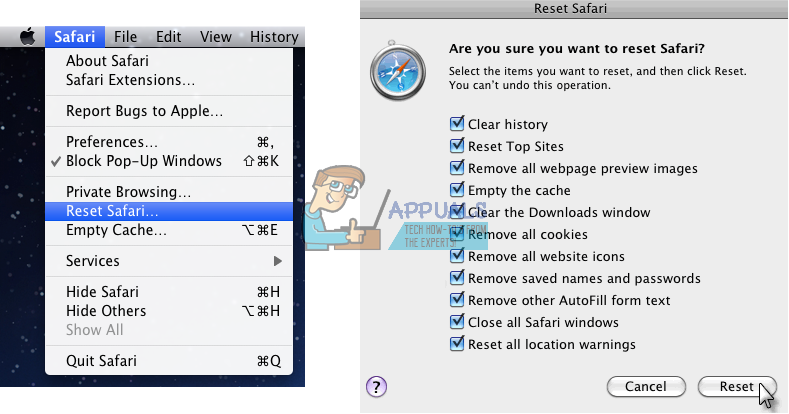
- On the Safari menu bar, click on Safari and choose Reset Safari. Now, make sure you select all boxes, and click Reset.
- For Chrome
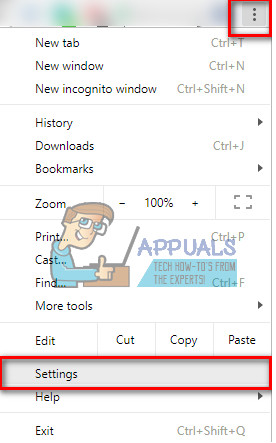
- While in Chrome click the menu icon and choose Settings.
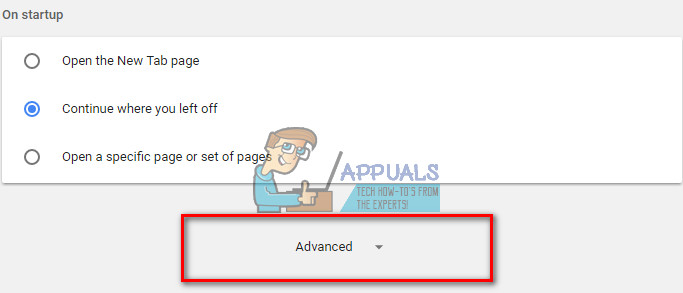
- Now, click on Show Advanced settings (at the bottom of the page).
- Then select Reset browser settings (at the bottom of the page).
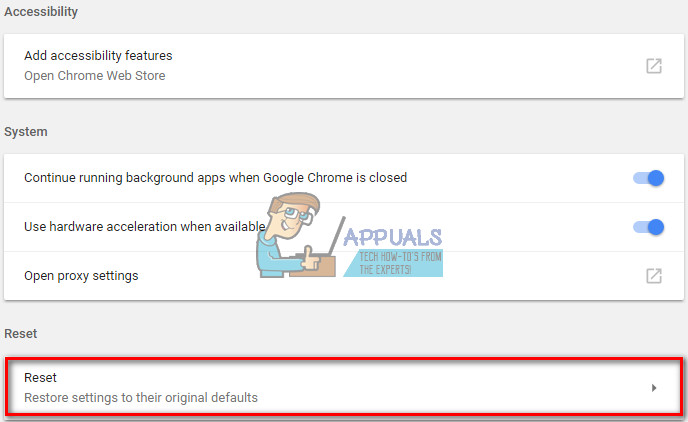
- Confirm by clicking Reset once again.
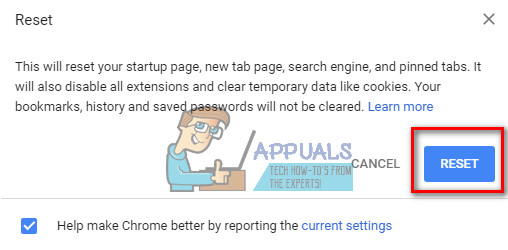
- While in Chrome click the menu icon and choose Settings.
- For Firefox
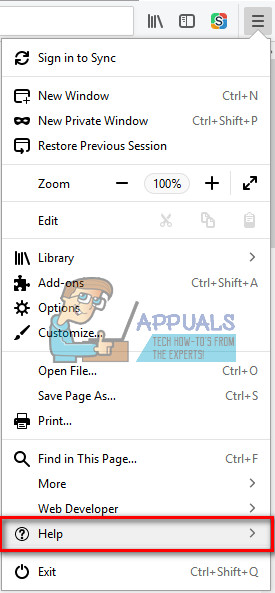
- While in Firefox click the menu button and click on Help.
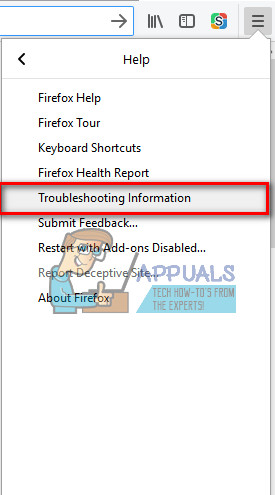
- From the next menu choose Troubleshooting Information.
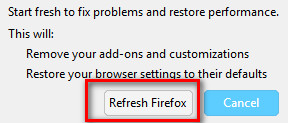
- Now, click on the Refresh Firefox… button in the top left area of the new page.

- Confirm your action by clicking on Refresh Firefox once again.
- While in Firefox click the menu button and click on Help.
Step #2: Download and Install Malwarebytes for Mac
Note: Malwarebytes for Mac works on macOS and Mac OS X 10.7 or later. If you are using this method, make sure you have a supported OS version.
- Download Malware from its official site (www.malwarebytes.com/mac/). DO NOT download any Malwarebytes files from untrusted sites. They worsened your situation.
- Once the download finishes, double–click the .dmg file to open it.
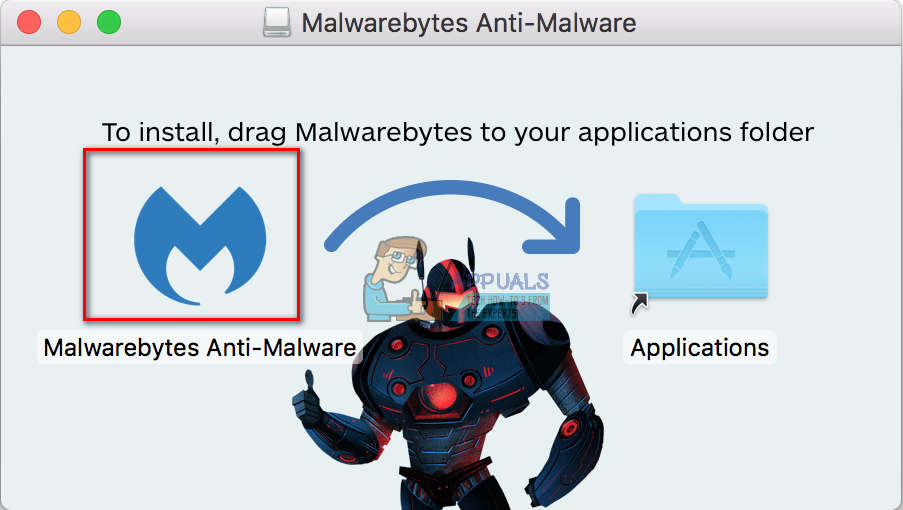
- Now, a window will appear showing you the Malwarebytes icon and your Applications folder. Drag and drop Malwarebytes onto the Applications folder.
Step #3: Scan your Mac using Malwarebytes
- Go to Applications (Click Go on the Mac menu bar and select Applications).
- Double–click the Malwarebytes icon. (or right-click it and choose open from the menu). If a prompt opens up (asking you if you are sure you want to open the app), click on open.
- Choose Agree in the next prompt. You will see this one if you are launching Malwarebytes for the first time on your Mac.
- Now, close all running programs on your Mac except Malwarebytes, and click on Scan.
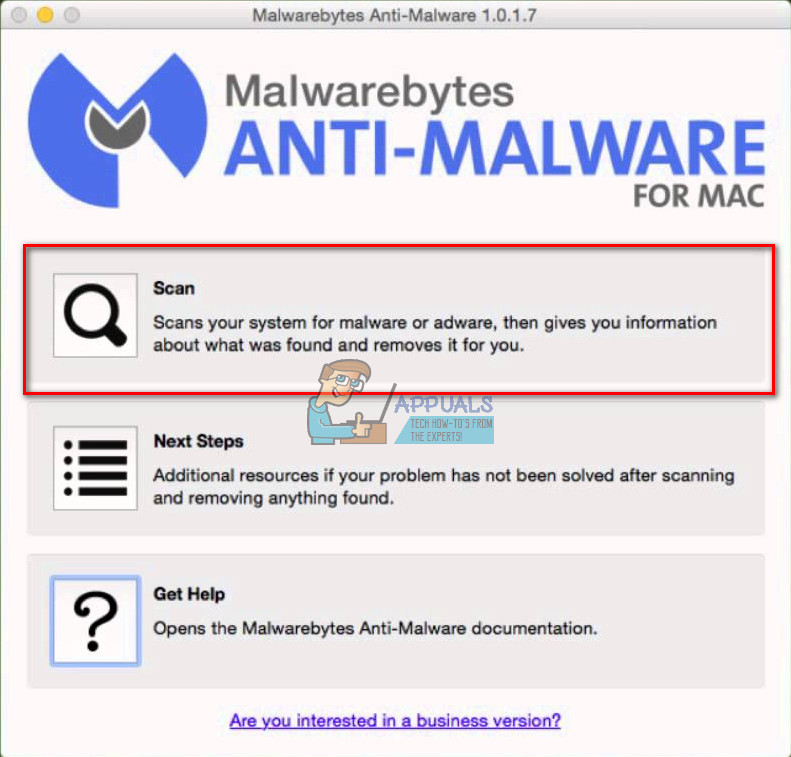
Once the scanning is done, the malware and adware apps should been removed.
Method #2 Manually Delete Malware (Advanced Users Only)
To remove DownLite trojan (or any other) malware from your Mac, you need to locate and delete its files.
Step #1: Locate the Malware (DownLite trojan) on your Mac
- Approach #1
- Triple–click on the text provided below, to select the whole string (line of text).
- /Library/LaunchAgents/com.vsearch.agent.plist
- Control + Click (or right–click) while the string is selected.
- Select Reveal in Finder (or just Reveal) from the menu.
- Triple–click on the text provided below, to select the whole string (line of text).
- Approach #2
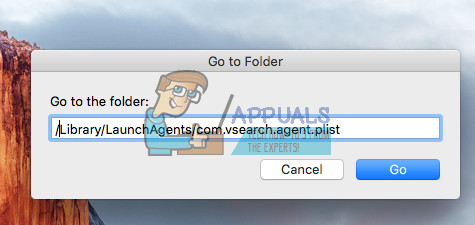
- If you do NOT see the contextual menu after clicking right click (or command + click), copy the selected text to the Clipboard (press Command + C).
- Now, click Go on the Finder menu.
- Select Go to Folder, and paste the text (press Command + V) into the box that opens up.
- Now press Return.
Step #2: Remove Malware from your Mac
- Once the Finder launches, a file (Vsearch) will be selected. Drag that file into the Trash, and type your administrator password if required.
- Repeat the procedure for each of the following files of DownLite trojan.
- /Library/LaunchDaemons/com.vsearch.daemon.plist
- /Library/LaunchDaemons/com.vsearch.helper.plist
- /Library/LaunchDaemons/Jack.plist
- Once you delete them, restart your Mac.
- Now, empty the Trash and repeat the same procedure for the following items:
Note: Some of the items may be absent. In that case, you will get a message that the file cannot be found. When this happens, just skip that item and continue with the next one.- /Library/Application Support/VSearch
- /Library/PrivilegedHelperTools/Jack
- /System/Library/Frameworks/VSearch.framework
- ~/Library/Internet Plug-Ins/ConduitNPAPIPlugin.plugin
- When you are done, restart your Mac again and empty the Trash.
The same procedure can be applied to other
malware programs. Here are some other known malware and the files that you need to delete to remove them from your Mac.
- ChatZum
- /Applications/ChatZumUninstaller.pkg
- /Library/Application Support/SIMBL/Plugins/SafariOmnibar.bundle
- /Library/Internet Plug-Ins/uid.plist
- /Library/Internet Plug-Ins/zako.plugin
- Conduit
- /Library/InputManagers/CTLoader/
- /Library/LaunchAgents/com.conduit.loader.agent.plist
- /Library/LaunchDaemons/com.perion.searchprotectd.plist
- /Library/Application Support/SIMBL/Plugins/CT2285220.bundle
- /Library/Application Support/Conduit/
- /Applications/SearchProtect.app
- /Applications/SearchProtect/
- ~/Library/Application Support/Conduit/
- ~/Library/Internet Plug-Ins/ConduitNPAPIPlugin.plugin
- ~/Library/Internet Plug-Ins/TroviNPAPIPlugin.plugin
- ~/Conduit/
- ~/Trovi/
- For Firefox
~/Library/Application Support/Firefox/Profiles/
Inside this folder open the folder that starts with random characters and ends with “default.” Now remove the following files:
js
takeOverNewTab.txt
searchplugins/[any file with “Conduit” in the name].xml
searchplugins/MyBrand.xml
- Spigot
- ~/Library/LaunchAgents/com.spigot.SearchProtection.plist
- ~/Library/LaunchAgents/com.spigot.ApplicationManager.plist
- ~/Library/Application Support/Spigot/
- OperatorMac
- ~/Library/Application Support/Google/Chrome/Default/chromex
- ~/Library/Application Support/Google/Chrome/Default/chromexdm
- ~/Library/Application Support/mediahm
- ~/Library/LaunchDaemons/com.mediahm.operator.update.plist
- For Firefox
~/Library/Application Support/Firefox/Profiles/
Inside this folder open the folder that starts with random characters and ends with “default.” Now remove “mySearchPlug.xml” if present.
Step #3: Clean up Safari, Chrome, and Firefox
- Launch Safari, and choose Preferences > Extensions from the Safari menu bar.
- Uninstall any extensions you don’t use or don’t recognize. Especially look for any that have the word “Conduit” or “Spigot” in the description. If in doubt, remove all extensions.
- For best results reset Safari (Safari > Reset Safari, make sure you select all boxes, and click Reset)
- Do the same procedure for Chrome and Firefox (if you use either of those).
DownLite trojan (and most of the other malware programs) are usually distributed on illegal websites that provide pirated movies. If Mac’s user opens up such sites and follows instructions to install software, that may further worsen the situation.
Gatekeeper doesn’t prompt any warning about installing DownLite trojan software. The reason is that the DownLite developer has a codesigning certificate issued by Apple. That’s why Gatekeeper doesn’t declare it as an unknown-developer and gives the installer a pass.
Note: Malware is continually changing to get around the defenses against it. The instructions given in this article are valid at the time of writing. But, they won’t necessarily be accurate in the future.