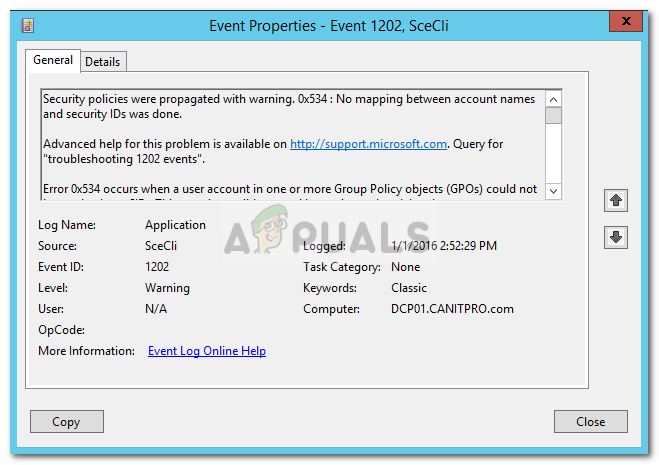
Fix: No Mapping Between Account Names and Security ID was Done
The error message “No Mapping between account names and Security ID was done” pops up when there’s a bad mapping between account names and security IDs in a domain. It occurs in the Microsoft Windows AD Group Policy (Active Directory Group Policy). If you look up this error message in the event viewer, it is labeled with the error code 1202.
To give you a brief insight into the error message, let us discuss what potentially causes it.
What causes the ‘No Mapping Between Account Names and Security ID was Done’ Error Message?
Well, the cause of the error is mentioned in the error message itself, however, to make more sense out of it, it is caused due to the following reasons:
- Incorrect Username: In some cases, the error message can be due to an incorrect username, therefore, before you proceed, make sure that the username is entered correctly.
- Group Policy Setting: Another possible cause of the error message is your Group Policy settings. To tell you in brief, it is caused by a GPOs setting which is used for a domain with orphaned accounts details due to which they can’t correctly resolve to SID.
Now there are two possible explanations for this, either the account name used in GPO has a typing error or the account used in GPO has been removed from the Active Directory. There are multiple ways using which you can solve this error but the important thing is that you should resolve the issue which is causing it.
Finding the Culprit Account and Tweaking the Group Policy Settings
In order to resolve the issue, first, you will have to locate the account which is causing the issue. That can be only done if you have the log file enabled. To do that, you will have to edit the ExtensionDebugLevel entry in the Windows Registry which will enable the log file. Here’s how to do it:
- Press Windows Key + R to open the Run dialog box.
- Type in regedit to open the Windows Registry.
- Afterward, search for the following entry by pasting the following path in the address bar:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions\{827D319E-6EAC-11D2-A4EA-00C04F79F83A} - Once done, double-click the ExtensionDebugLevel entry on the right-hand side and set its value to 2.
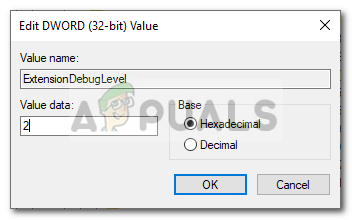
Changing the Value of the Entry to 2 - This will enable the log file.
- Now to find the account(s) that has the problem, enter the following command in the Domain Account Controller with Domain Administrator privileges:
FIND /I "Cannot find" %SYSTEMROOT%\Security\Logs\winlogon.log
- This will prompt you the account that is having the issue.
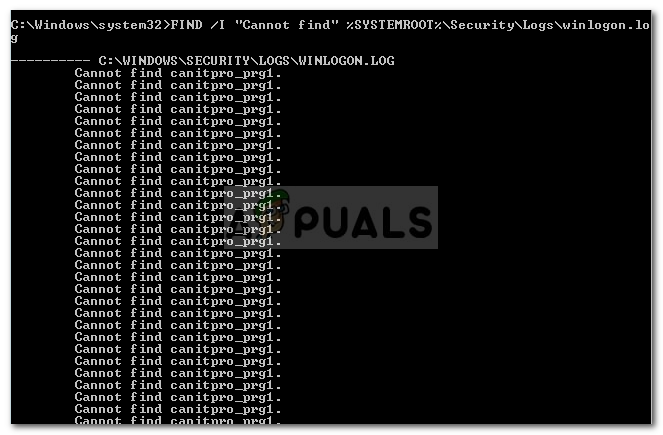
Finding the Account with the Issue - Once you have got the account name, you will have to check where the account is being used.
- For that, you will have to run the Resultant Set of Policy MMC. Open Run dialog box again as mentioned above, type in RsoP.msc and then hit Enter.
- In the Resultant Set of Policy window, navigate to the following directory:
Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment
- On the right-hand side, you will see a red cross. Double click on it.
- You will see the account name in it from earlier which is causing the issue.
- Now, there are two possible things. Either the account name is incorrectly typed in which case you will just have to rectify it. If that’s not the case, then you will have to check whether the account exists in the Active Directory. If it doesn’t, you will just have to remove it which will fix your issue.
- Once done, open up the command prompt as an administrator and run the following command to update the policy settings:
gpupdate /force
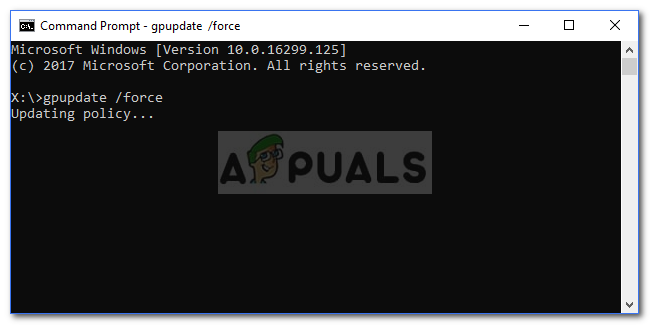
Updating Group Policy - Once the policy settings have been updated, you should be good to go.




