What is: CNG Key Isolation (lsass.exe)
The CNG (Cryptographic Next Generation) Key Isolation service provides key process isolation to private keys and a number of associated cryptographic operations as required by the Common Criteria. The default path to the executable associated with the CNG Key Isolation service is C:\ windows \ system32 \ lsass.exe.
CNG Key Isolation Explained
The CNG key isolation service runs as a LocalSystem in a shared process (hosted in the LSA process). The service stores long-lived keys to authenticate users in the Winlogon service. For example, the CNG Key Isolation service will store a wireless network key or the required cryptographic information for a smart card. All operations performed by the CNG Key Isolation service are performed by following the Common Criteria requirements.
In the event that the CNG Key Isolation service fails to load or initialize, the behavior is recorded in the Event Log. Most of the time, the service fails to start because the Remote Procedure Call (RPC) service is forcibly stopped or disabled. If the CNG Key Isolation service is stopped, the Extensible Authentication Protocol (EAP) will fail to start and initialize at startup.
As you’ll come to see below, the CNG key isolation service shares an executable (lsass.exe) with several other services.
What is Lsass.exe?
LSASS stands for Local Security Authority Subsystem Service. The genuine lsass.exe is a legitimate software component part of the Windows environment. The executable is regarded as a core system local authority process that is built into Windows. The default location os lsass.exe is in C:\ Windows \ System 32.
The Lass.exe process handles four main authentication services in Windows:
- KeyIso (CNG Key Isolation) – The most important authentication service hosted in the LSA process. It provides key process isolation to private keys and associated cryptographic operations.
- EFS (Encrypting File System) – A core file encryption technology mainly used to store encrypted files on NTFS file system volumes. Stopping this service will prevent your system from accessing encrypted files.
- SamSS (Security Accounts Manager) – The main purpose of this service is to act as a beacon and signal other services when the Security Account Manager (SAM) is ready to receive requests. Stopping this service will prevent other services relying on the Security Account Manager from being notified. This will create a snowball effect that will cause a lot of dependent services to fail or start incorrectly.
- Local IPSEC Policy – Manages and starts the ISAKMP/Oakley (IKE) and various IP security drivers in Windows Server.
Potential Security Risk with lsass.exe
Some Windows users find that the Lsass executable consumes a lot of system resources and suspect lsass.exe of being a virus or another type of malware. While this certainly possible, the chances are of this happening are slim.
However, there is a known copy-cat virus that has been known to infect systems by camouflaging into the Lsass executable. The process is similar, but not identical to the genuine Local Security Authority Subsystem Service. The malitious process is named isass.exe, as opposed to the legitimate process that is named lsass.exe. If you find that the process starts with a capital I instead of a lower case L, your system is probably infected.
You can confirm this theory by checking the location of lsass.exe. Generally, if the Lsass executable is located in C:\ Windows \ System 32, you can safely assume that it’s the legitimate Local Security Authority Subsystem Service. To do this open Task Manager (Ctrl + Shift + Esc) and scroll down in the Processes list to Local Security Authority Process. Right-click on it and choose Open file location. If the process is not located in System 32, you can be sure that you’re dealing with a malware infection.
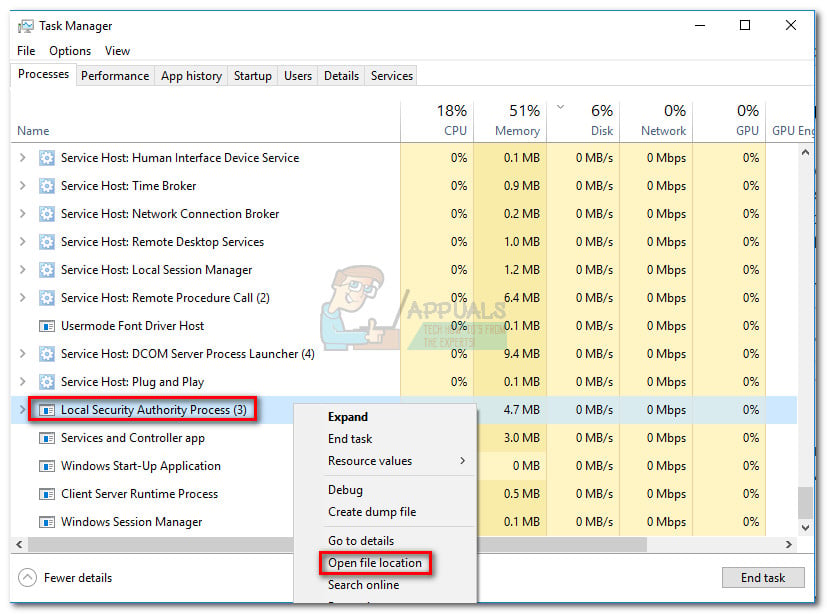
The “Isass.exe” is a trojan virus with keylogging properties known the Sasser worm family. Its main purpose is to quietly harvest data from your system. By registering every keystroke you type, the virus is configured to go after account usernames, passwords, credit card numbers and any other sensitive data that is ultimately used for an illegitimate financial gain.
The virus has been around for several years and Microsoft has already taken measures against it. If you find that you’re infected, you can use the Microsoft Malware Removal tool to remove any traces of the Sasser worm. After months of infecting countless Windows 7 and XP users, Microsoft has patched the vulnerability that allowed the virus to infect Windows machines. As of now, it’s no longer possible to get infected with the Sasser worm if you have the latest Windows security updates.
Should I disable the CNG key isolation service?
No. The CNG key isolation service is a critical system process needed to store cryptographic information securely. Under no circumstances should the legitimate CNG Key Isolation (KeyISO) Service should be permanently disabled.
Ending the lsass.exe process in Task Manager will also stop the CNG key isolation service. But keep in mind that this might cause your system to shut down forcibly. Since it controls the most important part of the log on security, the CNG key isolation is an essential function of Windows.
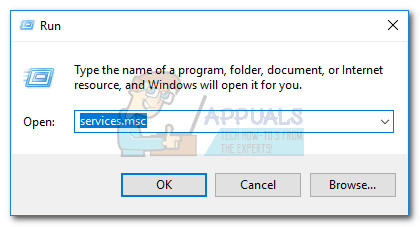
However, if you suspect that the CNG key isolation service is not functioning properly or is causing problems with your system, you can try to restart the service. To do this, open a Run window (Windows key + R) and type services.msc. Then, hit Enter to open the Services window.
In the Services window, scroll down to the CNG Key Isolation service. Right-click on the service and then choose Restart to force a reinitiation.
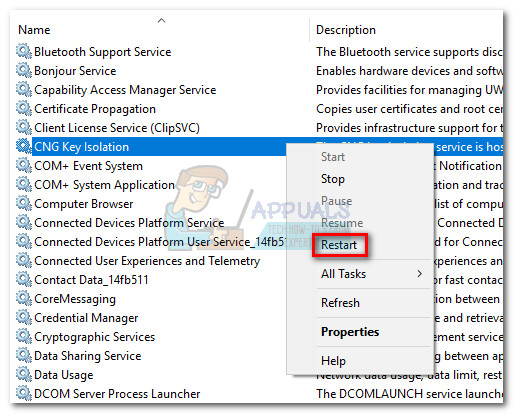
Note: Keep in mind that depending if the CNG Key Isolation service is currently in use, you might encounter an unexpected system reboot. Do not restart this service unless you have legitimate reasons for doing so.