How to Check if your Phone is Infected with Pegasus Spyware?
In the past few days, news about Pegasus Spyware has been trending all over the internet. This malicious utility was developed by the infamous Israeli hacking firm – NSO Group for Law enforcement agencies and Intelligence services to secretly spy on people from different countries.

A report from Information Security specialists shows that as of July 23rd, 2021, 50,000 phones and devices were infected by the Pegasus Spyware. Quoting this number against the world’s whole population doesn’t seem high, but the malware itself is dangerous. It gains full access to your phones’ system and reading data like photos, images, tap on conversations, read correspondence, and much more.
This revelation has got most Android and IOS users thinking of ways to check for the existence of this spyware on their phones. Unfortunately, most antivirus programs cannot detect this malware as it exploits Zero-day vulnerabilities, which are unknown to developers and hardware vendors. Luckily, Amnesty International, a Human Rights organization, has developed a Mobile Verification Toolkit (MVT) tool that you can use to scan your device for the pegasus malware. Its source code is available on GitHub.

The MVT is compatible with both Android and IOS. It can detect any Indicators of Compromise (IOCs) used by the Pegasus Spyware. Unfortunately, as of writing this post, there are no quick installation packages. You will need to compile and build the source code on your Linux or macOS computer. MVT’s capabilities are always improving as developers add more advanced features to the toolkit. As of writing this post, some of its most important features include:
- Decrypt encrypted iOS backups
- Process and analyze data from a variety of iOS systems, logs, application databases and system analytics.
- Android devices’ installed applications can be extracted for scanning
- Using the ADB protocol, you can get diagnostic information from Android devices.
- Compare the extracted records to a STIX2-formatted set of harmful indicators.
- Create JSON logs for all extracted records and separate JSON logs for all harmful traces found.
- Create a uniform chronological timeline of all retrieved records and a timeline of all malicious traces found.
Check If your Phone is Infected with Pegasus by using MVT
As discussed above, MVT is available only for Linux and macOS. I tried using Windows Subsystem for Linux (WSL), but it kept throwing the error “adb_shell.exceptions.UsbDeviceNotFoundError” whenever I tried to reach my phone. In this post, we will install MVT on Kali Linux. If you are on macOS, check out the installation guide on the MVT-docs website.
To get you started, we need to install the dependencies necessary for building and compiling all the required tools. Launch the Terminal and execute the commands below.
sudo apt install python3 python3-pip libusb-1.0-0
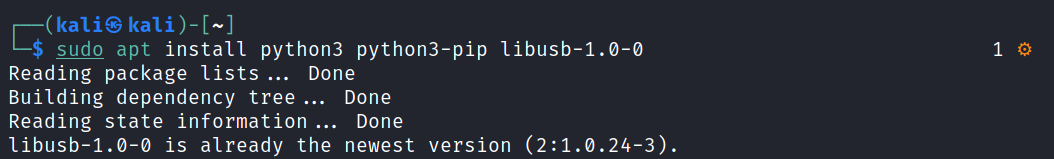
If you intend to use the MVT tool on an IOS phone only, you don’t need to install the libusb-1.0-0 library. Also, to locally download and install Pypi binaries in the $PATH, execute the command below:
export PATH = $PATH:~/.local/binNext, we will download the official source code and install MVT using pip. Execute the commands below:
git clone https://github.com/mvt-project/mvt.git cd mvt pip3 install
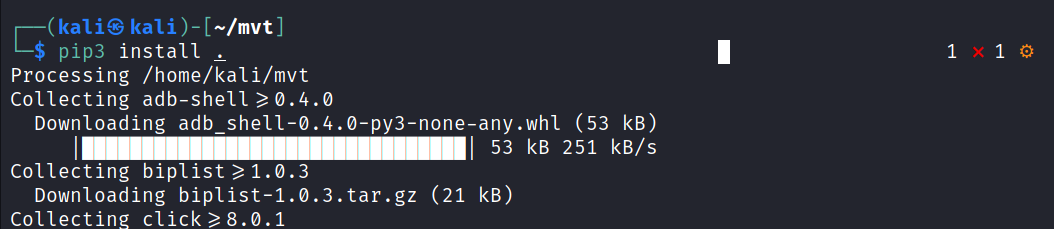
After the download completes successfully, you can now run the mvt-ios or mvt-android utilities to start scanning your devices.
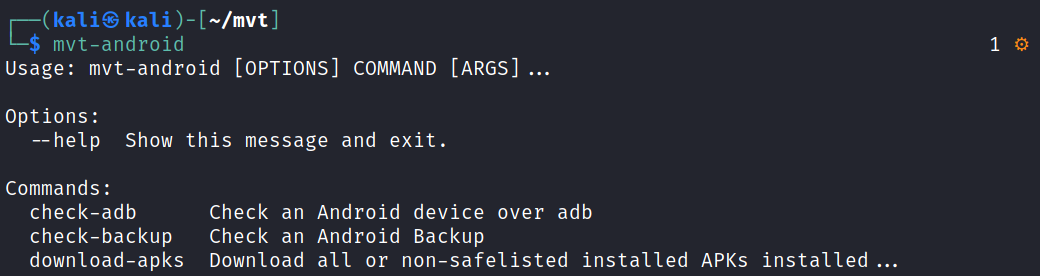
I believe this article has given you a clear guide on how to scan your phone for Pegasus Malware. Even though this malicious utility is becoming very popular, hundreds of spy applications run on user devices without their knowledge. Many apps operate as legitimate applications offering a useful service, but they are reading all important information on your device behind the scenes. Learn to practice digital hygiene and stay safe.





