How To Ensure Privacy And Safety Online
Most people are well acquainted with some classical software tools to ensure security on their computing devices. Thus, most computer users have a free or paid antivirus to filter for malicious content in data traffic or in the internal environment of the device (RAM, storage, including detachable disks, core OS processes, etc.). A firewall is typically integrated either in the antivirus or in the OS (if there are more firewalls, typically, only one is active). However, an antivirus or firewall does nothing to ensure online privacy.
VPNs Are Essential For Both Privacy And Safety
Nowadays, any user that thinks about going completely private online but also about ensuring truly comprehensive online safety (because the first contributes to the second) has to consider using a VPN. There are multiple providers on the market, both free and paid, with the latter providing more extensive functionality.
There are significant concerns with regard to Internet privacy in the recent period, given the possibility for accidental leakage of sensitive data, or the diversity of hacking attempts that can be aimed at identifying users and stealing important data from them. Alarmingly, not only individual users with malicious intent can be behind such attacks, but also resourceful mass surveillance government agencies (like NSA, or equivalent divisions in many authoritarian regimes).
![]()
How Do VPNs Work
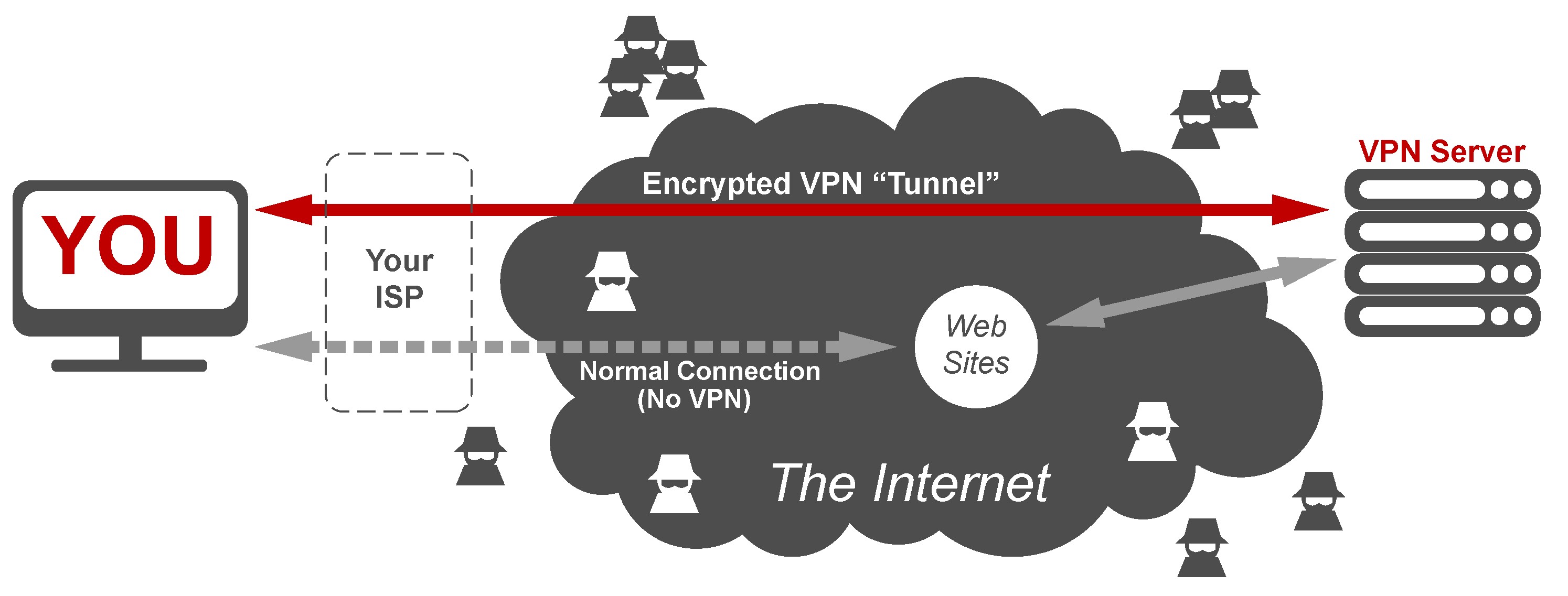
VPNs create safe encrypted communication channels between the user and the Internet, hence, any ill-intentioned third party would have big trouble intercepting and decrypting this traffic. Moreover, given that the traffic is routed via a dedicated VPN server, the physical IP address of the user is hidden from websites and any other online entity. The user can typically select the location of the VPN server from a list of countries and thus, can appear online as a user from the respective country.
The last trait comes as a significant bonus and one of the main reasons VPN services are contracted – adopting the IP address of a given country allows to bypass country-specific geographic restriction for lots of websites including YouTube, Netflix, etc. This aspect is also of paramount importance for users located in countries with the severely restricted Internet, with a vast list of banned foreign websites.
Choosing A VPN Provider
Different providers come with different features and choosing the most suitable one obviously depends on the specific needs one has, although most top players on the market offer rather balanced solutions that would satisfy a variety of needs. Typical features that are of interest when choosing a provider are as follows:
- the strength of the encryption protocol (e.g. OpenVPN, L2TP/IPSec, SSTP, IKEv2, PPTP);
- the length of the encryption key (e.g. AES 256-bit key);
- the number and type of devices (and OSs) covered, including PCs, laptops, smartphones, tablets, TV boxes, routers, etc.;
- the number and choice of countries where VPN servers are located (especially relevant for avoiding geographic bans);
- the log policy (if logs are kept, what information is logged and how is it protected);
- availability of unique features (such as “kill switch”, ad blockers, etc.);
- availability of a trial period for the fully functional product;
- the price for the monthly/ seasonal/ yearly subscription.
As it can be noticed, the features listed above are related both to the level of safety and convenience. The specific combination of desired traits should dictate the choice of the VPN provider.